A Cyber Threat Intelligence Recap for COVID-19 in 2020

Much has been said about the COVID-19 pandemic. In many ways, it has changed the way we live, work, or simply interact with our relatives and friends. From the standpoint of cybersecurity, the pandemic also had a strong influence on how threat actors and cybercriminals created and executed all types of cyberattacks and phishing campaigns.
To illustrate, this post features a timeline of COVID-19-related cyber threats and some cyber threat intelligence found for each month of 2020.
January 2020: The Appearance of Remote Working-Related Threats
As many companies transitioned to remote working setups, security analysts and researchers noticed an increase in the number of COVID-19-themed phishing emails. Some 13% of the social engineering attacks seen in the first quarter of the year were, in fact, coronavirus-related.
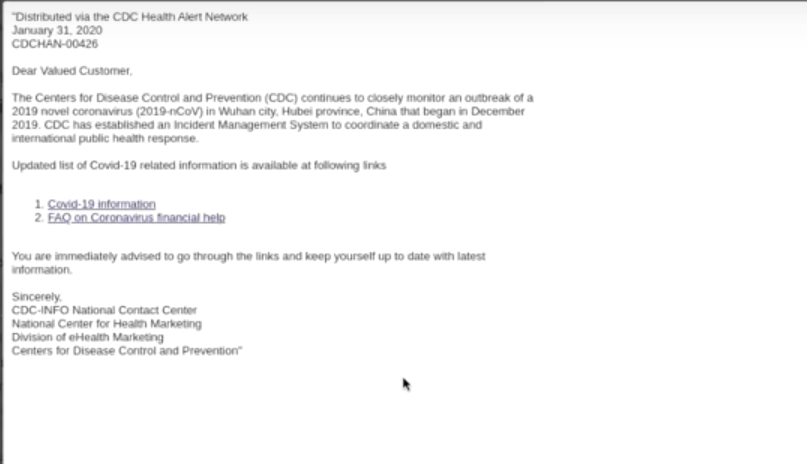
Phishers are known for mimicking reputable organizations so the former would appear as their malicious emails’ senders. That was the case of the phishing email below supposedly from the Centers for Disease Prevention and Control (CDC). By relying on the trust that both individuals and companies alike endow on reputable message senders, threat actors are able to breach target networks and steal the confidential data they keep.
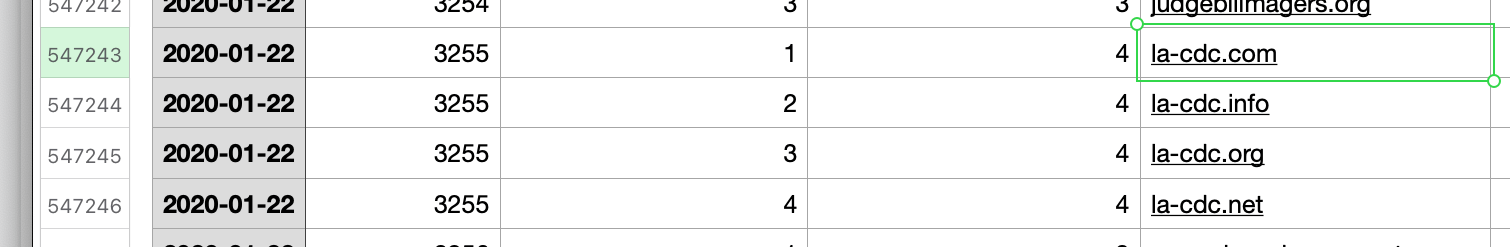
Regular monitoring typosquatting data feeds can help detect copycat domains registered in bulk. A look at the typosquatting data feed for January 2020, for example, lists down these domains which resemble those of reputable healthcare organizations that could be used in phishing campaigns:
- la-cdc[.]com, la-cdc[.]info, la-cdc[.]org, and la-cdc[.]net, bulk-registered on 22 January 2020, which could be used to trick users into thinking an email is from the CDC’s Los Angeles office
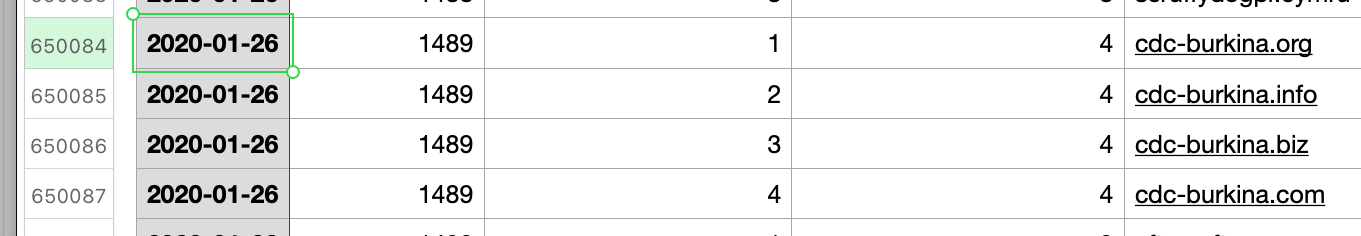
- cdc-burkina[.]org, cdc-burkina[.]info, cdc-burkina[.]biz, and cdc-burkina[.]com, bulk-registered on 26 January, which could be used for campaigns targeting beneficiaries of the CDC’s activities in Burkina-Faso
February 2020: An Upward Trend in Coronavirus-Themed Domain Registration
That month saw an uptick in COVID-19-themed domain names that contained strings like “help,” “antibiotics,” “avoiding,” “anti,” and “graph”. While some of their owners were not ill-intentioned, others like the following ended up part of cyberattacks that put end users and organizations at great risk:
- helpcoronavirus[.]com, a confirmed phishing domain registered on 1 February
- antibioticsforcoronavirus[.]com, a confirmed phishing domain registered on 2 February
- avoidingcoronavirus[.]com, a confirmed phishing domain registered on 3 February
- anticoronaviruses[.]com, a confirmed phishing domain registered on 4 February
- coronavirusgraph[.]com, a confirmed phishing domain registered on 5 February
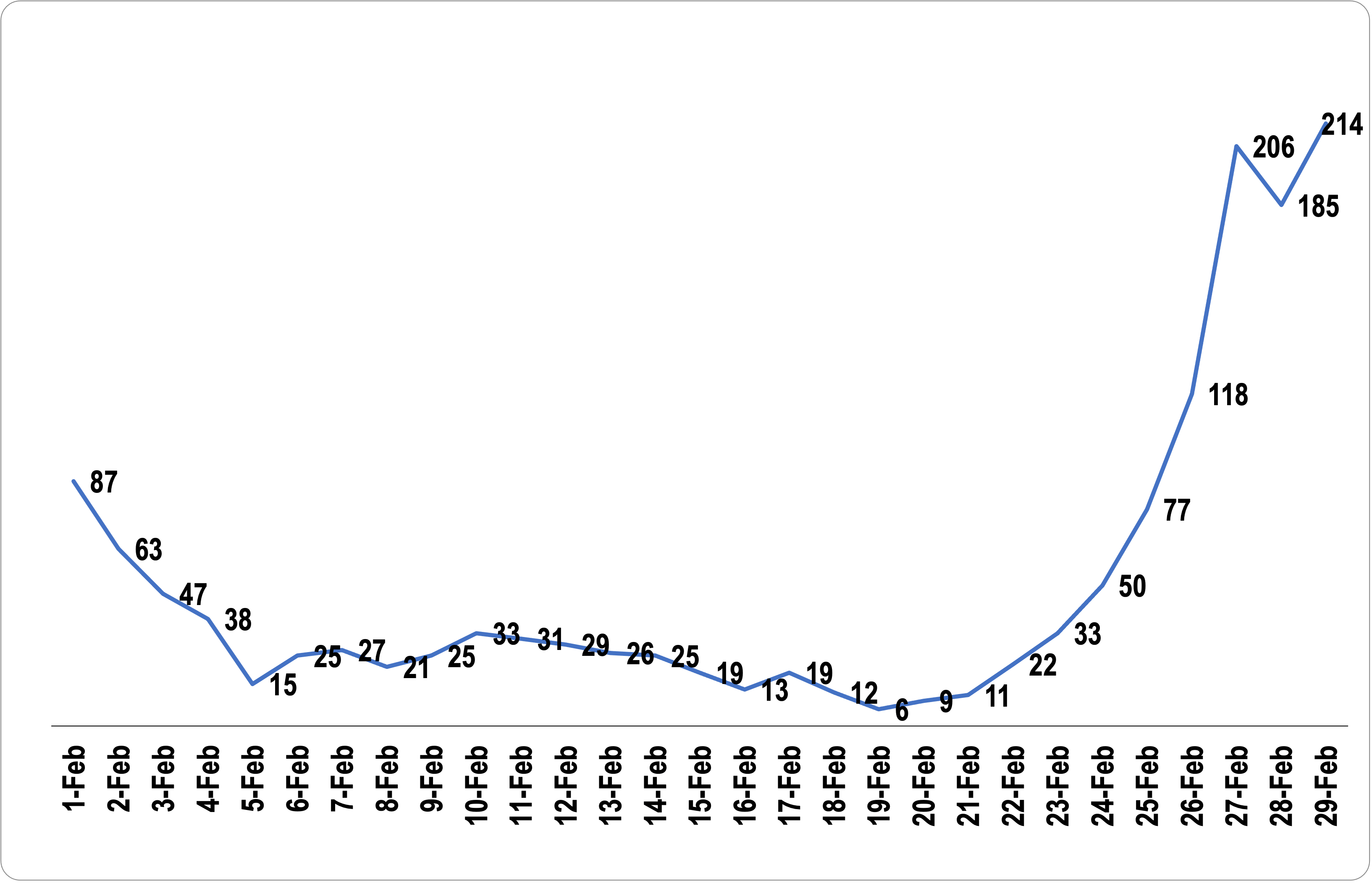
There are plenty of others (especially if we include misspelled variations of the strings mentioned and other terms pertaining to the disease like “COVID-19”) in each daily feed. The figure below shows the total number of domains with the string “coronavirus” just for the .com top-level domain (TLD) seen in February 2020, which reached over 200 daily by the end of the month.
March 2020: A Targeted Attack Hits the U.S. Health and Human Services Department
The U.S. Health and Human Services Department (HHS) was the victim of a cyberattack that aimed to disrupt the agency’s services and spread disinformation to undermine the government’s response to the pandemic. Some believe the attack was the handiwork of foreign threat actors.
While initial investigations revealed no data has been breached, the attack may have begun with a distributed denial-of-service (DDoS) attempt. Later on, social media posts warning people of an impending national lockdown supposedly from the HHS spread. Upon discovery, however, the agency corrected this rumor.
Over the years, cyber attackers have used a number of malware variants to target the HHS. Among these are Emotet, TrickBot, Ryuk, Maze, and Gh0st RAT. We sought to find Emotet indicators of compromise (IoCs) that similar government institutions should be wary of and found the following malicious IP addresses:
- 163[.]53[.]204[.]180
- 125[.]0[.]215[.]60
- 89[.]163[.]210[.]141
- 157[.]245[.]145[.]87
- 203[.]157[.]152[.]9
When subjected to reverse IP/DNS lookups, we obtained a list of 10 URLs that organizations might want to steer clear of.
We also obtained the domain imedu[.]org, which yielded two relevant subdomains based on a domain and subdomain discovery lookup—imedu-hubs-01-cors-proxy[.]imedu[.]world and imedu-hubs-01-app[.]imedu[.]world.
April 2020: Attacks against U.S. Hospitals and Labs Attempt to Steal Vaccine Information
The U.S. government’s cybersecurity analysts saw increased cyberattack activity that they believe had to do with attempts to steal coronavirus vaccine-related research. One advanced persistent threat (APT) group, in particular, was named APT41.
Among the IoCs FireEye disclosed in connection to the attacks are the IP addresses 66[.]42[.]98[.]220, 91[.]208[.]184[.]78, and 74[.]82[.]201[.]8 and the domain exchange[.]dumb1[.]com.
According to reverse IP/DNS lookups, the IP addresses are also connected to 74[.]82[.]201[.]8[.]16clouds[.]com and accounts[.]longmusic[.]com, apart from the domain FireEye named a threat IoC.
May 2020: Major Ransomware Operators Promise to Stop Attacks against Healthcare Institutions
In May 2020, major ransomware operators said that they would stop going after healthcare institutions during the pandemic. Some even vowed to provide decryptors should said potential targets get infected with their creations.
Note, though, that the ransomware variants major groups like Maze create and use in their attacks are not exclusive. Individual attackers and run-of-the-mill cybercriminals can end up using them, too. As such, we expanded the list of IoCs the Maze ransomware operators are connected to. We obtained the following list of confirmed malicious Maze-related IP addresses from VirusTotal:
- 91[.]218[.]114[.]25
- 91[.]218[.]114[.]26
- 91[.]218[.]114[.]11
- 91[.]218[.]114[.]4
- 192[.]124[.]249[.]41
- 72[.]21[.]91[.]29
- 72[.]21[.]81[.]200
Reverse IP/DNS lookups revealed that these are connected to 28 domains that may be worth including in organizations’ blacklists.
June 2020: As the Pandemic Ensues, Coronavirus-Related Domain Registrations Soar
Six months into the year and as vaccine manufacturers get closer to their goal of producing a remedy, cybercriminals continue to take advantage of the panic and shift to remote work setups, launching attacks aided by newly registered domains (NRDs).
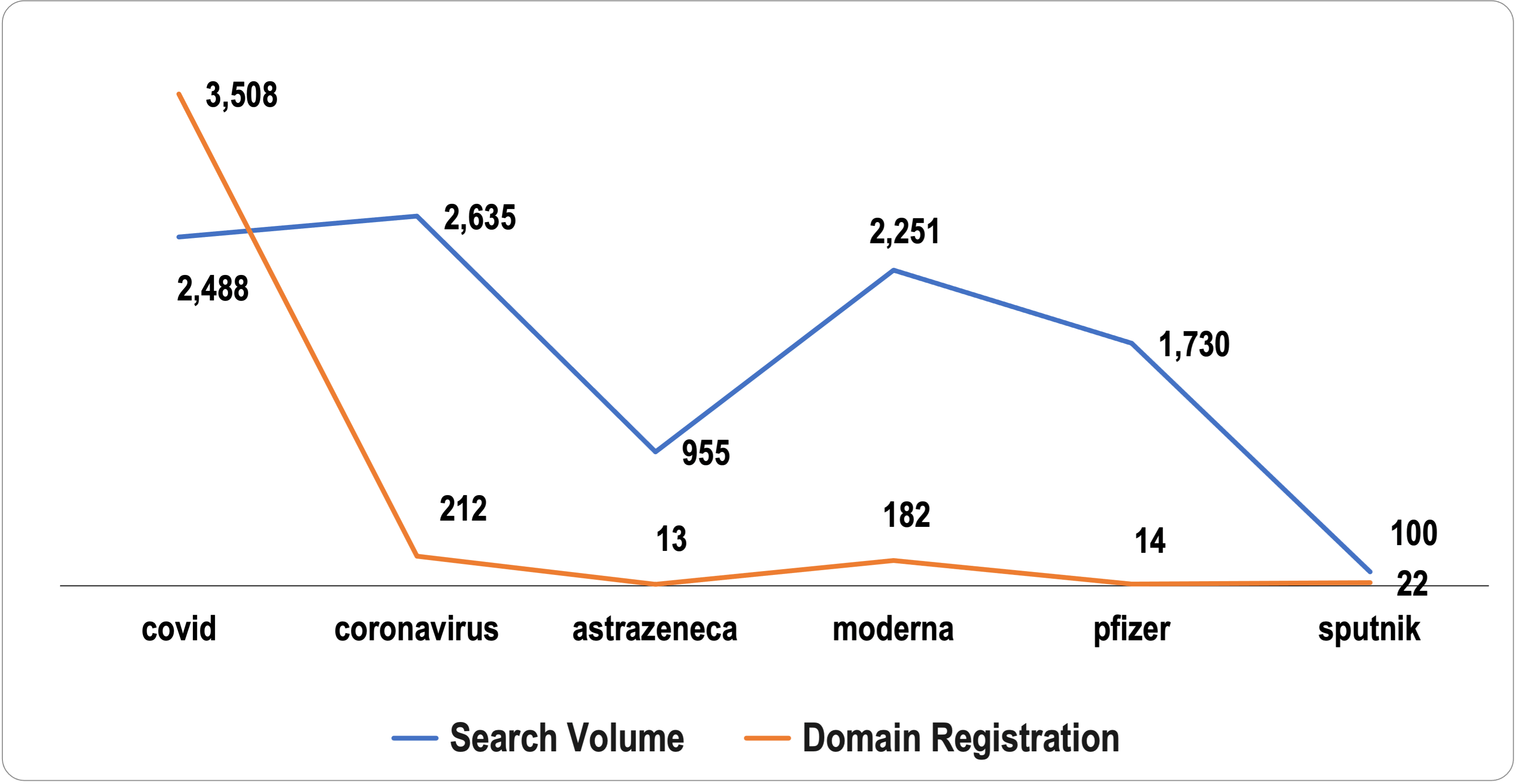
A look into the .com domain registration trend for June 2020 shows a continuous upward trend from previous months for domain names that contain the strings “coronavirus” and “covid.” And since companies and government-funded institutions started announcing vaccine trials, strings like “astrazeneca,” “moderna,” “pfizer,” and “sputnik” were added to the list.
We sought to compare if news and announcements affected domain registration trends. In particular, we wanted to know if the volume of public interest in a topic or company (based on the popularity of a search term on Google Trends) influences domain registration (according to the number of NRDs containing the same terms). We found that the more popular a search term is, the more domain names containing it are registered.
July 2020: APT29 Targets Coronavirus Vaccine Scientists to Steal Research Data
In the second half of the year, multiple government agencies from the U.K., the U.S., and Canada reported that a Russia-linked hacking group called “APT29” was targeting COVID-19 vaccine development organizations via spear-phishing campaigns. The group specifically targeted scientists involved in researching and producing vaccines.
Some 53 IP addresses were tagged as IoCs that distributed WellMess and WellMail malware, including:
- 209[.]58[.]186[.]196
- 209[.]58[.]186[.]197
- 209[.]58[.]186[.]240
- 220[.]158[.]216[.]130
- 27[.]102[.]130[.]115
The IP geolocation of about 30% of the IP addresses is Hong Kong, followed by Switzerland with an 8% share. Malaysia, China, the Netherlands, and Lithuania account for 6% of the IoCs, while the rest are divided between 17 other countries.
Bulk IP Geolocation GUI further revealed that the IP addresses are associated with 18 domain names, including:
- l250657a[.]justinstalledpanel[.]com
- vpn790641964[.]softether[.]net
- musicparadisepros[.]org
- v1[.]kimiad[.]vn
- mp3dler[.]com
August 2020: Ventilator Manufacturer Hit by Ransomware
By August 2020, cyber threats continued to loom over the healthcare industry. One of the most petrifying events then was the DoppelPaymer ransomware attack against Boyce Technologies, Inc. Boyce, originally a transit communication system manufacturer, decided to build ventilators in light of the COVID-19 pandemic.
Because of DoppelPaymer’s involvement in several ransomware attacks, such as those targeting Visser Precision and Newcastle University, cybersecurity researchers recently released three hashes as IoCs:
- 624255fef7e958cc3de9e454d2de4ae1a914a41fedc98b2042756042f68c2b69
- 624255fef7e958cc3de9e454d2de4ae1a914a41fedc98b2042756042f68c2b69
- c66157a916c7f874bd381a775b8eede422eb59819872fdffafc5649eefa76373
The last hash in the list contacted two IP addresses—148[.]251[.]213[.]132 and 5[.]9[.]198[.]84, both of which are geolocated in Germany. Reverse IP Search found eight connected domains.
| IP Address | Connected Domains |
| 148[.]251[.]213[.]132 |
|
| 5[.]9[.]198[.]84 |
|
While only static[.]84[.]198[.]9[.]5[.]clients[.]your-server[.]de has been reported malicious on VirusTotal, the other domains and the IP addresses may warrant close examination as well.
September 2020: Universal Health Services Hospitals Hit by Ransomware
Universal Health Services (UHS), one of the largest hospital chains in the U.S., became a target of a cyberattack that led to its IT network’s shutdown. The attack affected about 400 health systems, including ambulance services and the delivery of lab test results. It took its IT team three weeks to bring all the systems back online.
Cybersecurity researchers believed that the attack could be attributed to Ryuk ransomware likely distributed via phishing emails. That led us to ask: what was the domain registration trend for UHS hospitals’ look-alike domains months before the hit?
To investigate, we looked at six random UHS facilities and ran related keywords on Reverse WHOIS Search to see domains registered between 1 January and 25 September 2020, the day before the attack.
| Facility Name | Official Website | Keyword Used | Number of Look-Alike Domains Registered on 1 January–25 September 2020 |
| Valley Health Physician Alliance | valleyhealthphysicians[.]com | valleyhealth | 125 |
| Alliance Health Center | alliancehealthcenter[.]com | alliancehealth | 48 |
| Valley Hospital Medical Center | valleyhospital[.]net | valleyhospital | 23 |
| Arbour Senior Care | arbourseniorcare[.]net | arboursenior | 2 |
| Aiken Physicians Alliance | aikenphysicians[.]com | aikenphysician | 1 |
| Aurora Pavilion Behavioral Health Services | aikenregional[.]com/services/behavioral-health-services | aurorabehavioral | 1 |
Some of the facilities revealed dozens of domain registrations. However, some only had one or two look-alike domains registered within the almost nine-month period. Upon further scrutiny, the domains looked suspicious, since they didn’t share the same WHOIS record details as the official domains. Some of these domains were also parked.
October 2020: Trickbot Targets the Healthcare Sector
Cyberattacks against the healthcare sector continued in October, with victims going beyond UHS hospitals. The Federal Bureau of Investigation (FBI) even released an advisory warning to the healthcare sector of ransomware activities using Trickbot. Among the IoCs in the advisory were:
- kostunivo[.]com
- chishir[.]com
- mangoclone[.]com
- onixcellent[.]com
- 23[.]95[.]97[.]59
- 51[.]254[.]25[.]115
- 193[.]183[.]98[.]66
- 91[.]217[.]137[.]37
- 87[.]98[.]175[.]85
The IP addresses had five related domains, thus possibly expanding the list of Trickbot IoCs with new artifacts. Furthermore, DNS Lookup results for the domains returned four IP addresses, all of which are tagged malicious on VirusTotal.
November 2020: Microsoft Names 3 APT Groups Targeting COVID-19 Vaccine Makers
Highlighted this month is Microsoft’s mention that three APT groups are behind several cyberattacks targeting the healthcare industry. These groups are APT28 (also known as “Fancy Bear” or “Sofacy”), the Lazarus Group, and Cerium. Although Microsoft did not reveal IoCs related to these groups, we found a few associated with the first two.
Sofacy is known for using the heavily obfuscated malware Zebocry, delivered through COVID-19-related documents, in campaigns. Most of the IoCs are hashes, except for one, the URL https[:]//support-cloud[.]life/managment/cb-secure/technology[.]php. The DNS Lookup result for the domain pointed to IP address 80[.]90[.]39[.]24, which further led us to three other domains based on Reverse IP Search results.
For the Lazarus Group, eight URLs were tagged as IoCs. The historical WHOIS records of the root domains reveal that the registrants mostly use either Naver or Hanmail to register them. Of the eight domains, only five were reported malicious on VirusTotal, so we looked up their DNS records to obtain their IP resolutions and identified close to 180 associated domains.
| Malicious Domain | IP Address | Number of Associated Domains |
| ikrea[.]or[.]kr | 211[.]174[.]62[.]33 | 63 |
| quecue[.]kr | 115[.]68[.]122[.]150 | 13 |
| erpmas[.]co[.]kr | 222[.]231[.]63[.]93 | 5 |
| fored[.]or[.]kr | 211[.]218[.]150[.]75 | 94 |
| gongsinet[.]kr | 125[.]141[.]151[.]146 | 9 |
December 2020: Vaccine-Related Cyber Attacks and Scams and Increased Vaccine-Related Domain Registration
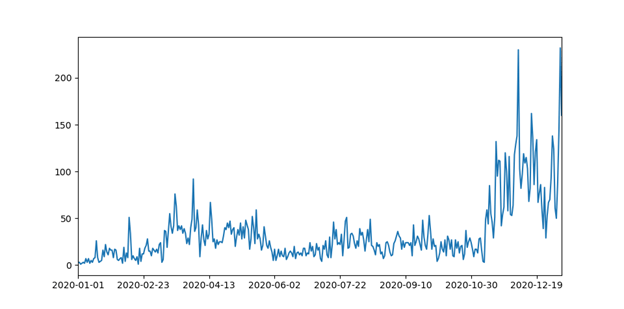
COVID-19 vaccines have been a hot topic throughout the year, but the registration trend for domains containing the word “vaccine” peaked in December which is when vaccination campaigns already started in some countries. We expect that was a significant driver in the spike of vaccine-related domain registration. The chart below reflects the trend.
The following chart, meanwhile, shows public interest over time using Google Trends for the search term “vaccine.”
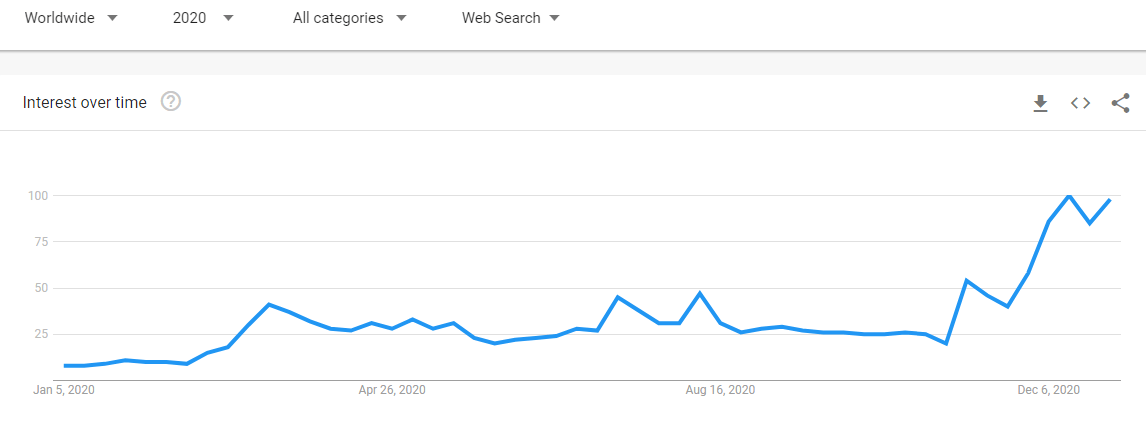
The trends in the charts above are similar, alluding to the fact that people’s interest in a particular topic greatly impacts domain registration.
---
The COVID-19 pandemic brought major healthcare-related and economic issues, but its impact was also felt in the virtual world. Cybersecurity experts have seen as many as 4,000 cyber attacks per day since the pandemic started, a 400% increase compared to the period before the outbreak. The threats featured in this post comprise only a fraction of what was truly going on in cyberspace.



































