Brand Monitor and Brand Alert API: How to Combat Brand Misrepresentation in the Retail Fashion Industry

Misrepresentations together with negative brand equity are probably the biggest nightmares of today’s most prominent companies — and more often than not, that’s connected to cybersecurity and data breaches.
For example, the latest stats show that one in every 99 emails you get each day has ties to a phishing attack, the majority of which come laced with malware specially crafted to harvest victims’ financial credentials or use popular brands as social engineering bait.
A great example would be an email offering a considerable discount that the victim may find very hard to resist. So she clicks the link to a site where she’s asked to fill in her personal data, including the credit card, for instance, that she plans to use to purchase goods. She doesn’t get the items she supposedly bought and so complained to the store via all possible means — email, phone, and social media.
What’s worse, others who fall for the same ruse join the frenzy, dragging the brand’s name through the muck. What can the victimized company do? Could it have prevented the phishing attack? These are just some of the things this article answers by analyzing Zara’s real-life case study.
Table of Contents
- The Attack: A Curious Case of Zara
- The Real Deal: Behind the Scammers’ Curtains
- The Evidence: Could Brand Monitor or Brand Alert API Have Helped Prevent the Attack?
- The Verdict: Lessons Learned from Zara’s Case
The Attack: A Curious Case of Zara
In the not-so-recent past, phishing was limited to emails that people usually read on their computers. That’s no longer the case though, since the birth of smartphones and the millions of apps that users can choose from as Zara’s case shows.
The Victim
Zara is a very popular Spanish fast-fashion retailer worldwide. Apart from having physical stores in some of the biggest shopping malls the world over, it also sells clothing and accessories via country or regional sites online. To date, it has a total of 202 physical and virtual shops.
The Attack Vector
WhatsApp is a messaging app that’s currently being used by hundreds of millions of users worldwide. It can be used on not only smartphones, but also personal computers, so just imagine the number of potential victims a cybercriminal could have.
The Bait
Sometime in February 2016, several WhatsApp users received an instant message from someone they know and trust prodding them to forward it to 10 contacts. They were then asked to click a shortened link to a site where they could get their free Zara gift cards.
The Real Deal: Behind the Scammers’ Curtains
Here’s how the victims’ credit card and other personally identifiable information (PII) landed on the phishers’ laps:
- 1. Potential victims got the following WhatsApp instant message from a contact.
![Potential victims got the following WhatsApp instant message from a contact. Potential victims got the following WhatsApp instant message from a contact.]()
- 2. They forwarded the message to 10 contacts as suggested (unknowingly getting more potential victims for the phishers).
- 3. They then click the shortened link to the site to get their free gift card (typically US$500 worth).
- 4. The site (specially crafted to look like a real Zara page) asks them to fill in a form to receive the gift card and so they do.
- 5. They click “Submit”, which sends their details to the attackers. Their personal information could then end up for sale in the Deep Web or underground marketplaces, be used by the phishers themselves for fraud, or be held for ransom.
This case isn’t the first time Zara’s or other popular retailers’ brand was used for a phishing attack. A similar ruse taking advantage of Zara was seen on Facebook even earlier, specifically, in March 2014. The message appeared on potential victims’ timelines. Those fooled into clicking the link were led to a site that harvested their personal information, including their credit card details.
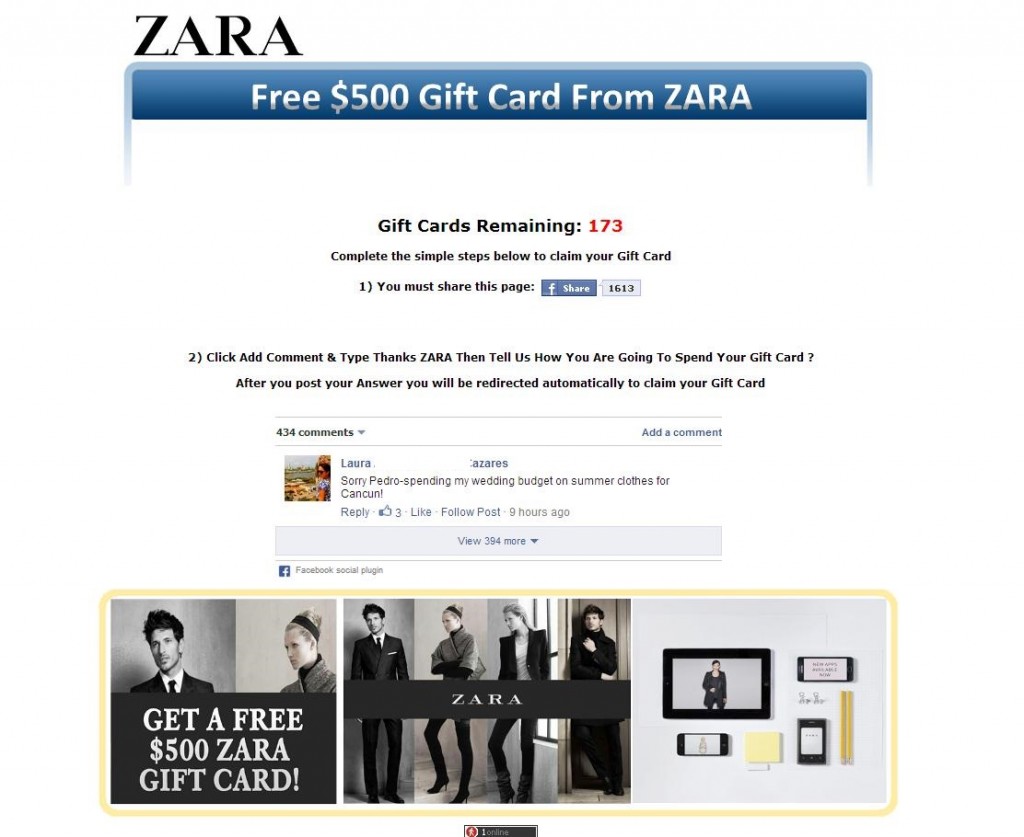
Regardless of the platform and brand used, one thing always remains: it’s a sham! None of the victims ever get gift cards, of course, they just end up inviting more people to get phished and handing their personal information to eagerly waiting cybercriminals via their specially crafted data-stealing sites.
The prospect of getting something for free always seems to do the trick when baiting digital citizens to give up their PII. They aren’t the only ones who suffer from phishing attacks, however. The retailers’ brands and thus, their reputations, also become casualties. So now we come to the burning question: Could Zara have prevented the phishing attack from its end using Brand Monitor or Brand Alert API? Let’s find out.
The Evidence: Could Brand Monitor or Brand Alert API Have Helped Prevent the Attack?
Brand Monitor is a domain-monitoring tool that lets users keep track of their brands’ and other trademarks’ or intellectual properties’ exact matches and variations, including those with all possible typos, to protect their business online.
Let’s see how it could have helped in Zara’s case:
- 1. Sign up by clicking “Open Dashboard” on the Brand Monitor site. You automatically get free Domain Research Suite (DRS) credits.
- 2. Look for and click “Brand Monitor” on the left panel. You’ll automatically be taken to the “Basic” function. Type your brand name in the input box, then click “Add to monitoring”. In this step-by-step guide, we’ll use the brand “Zara”. Note that you’ll need to wait for 24 hours to see the results because the monitoring is completed daily.
![Look for and click “Brand Monitor” on the left panel. Look for and click “Brand Monitor” on the left panel.]()
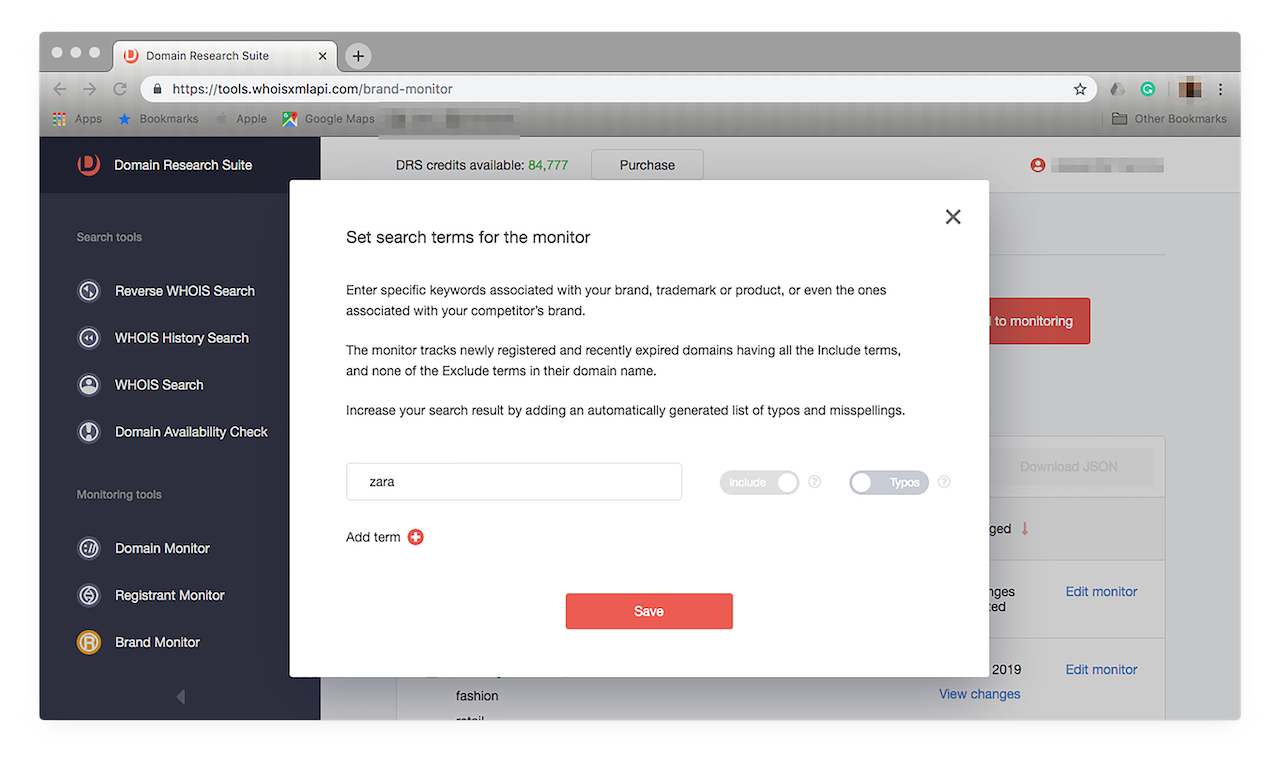
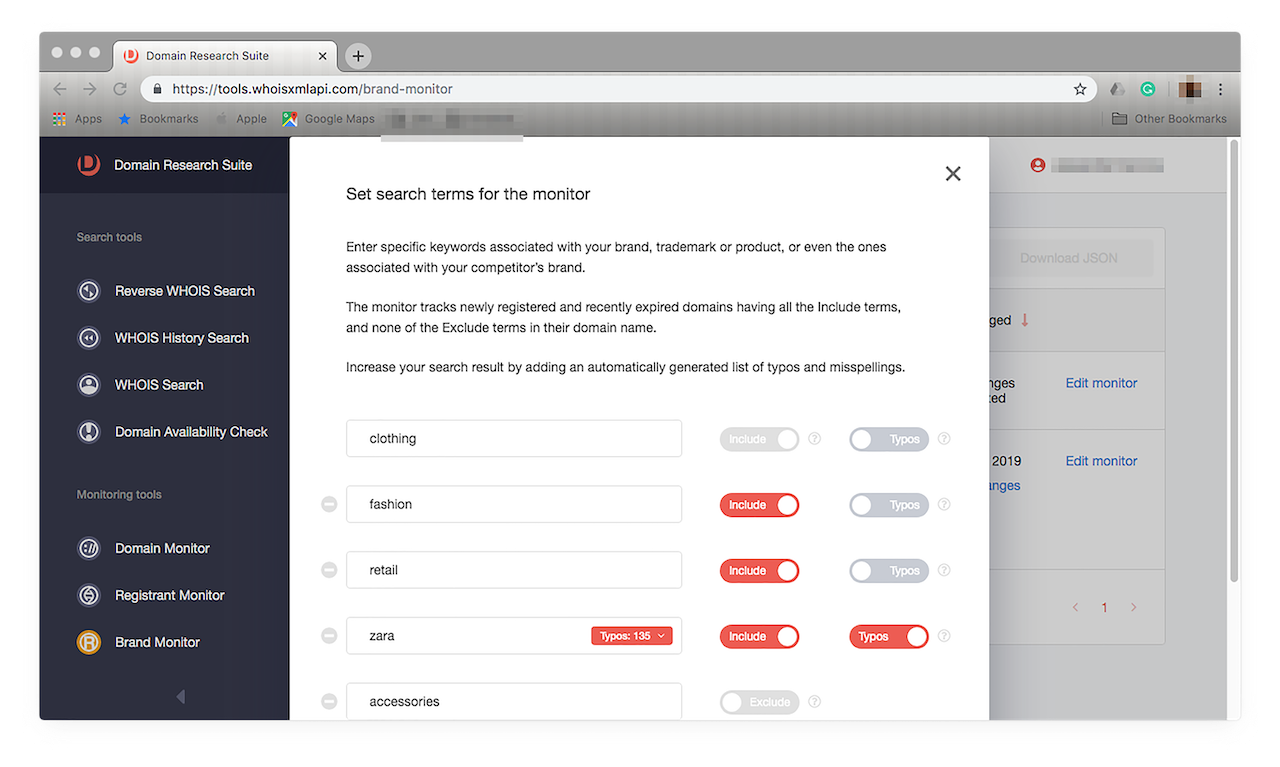
- 3. You can, however, already choose to use Brand Monitor’s Typos function. This feature helps if you’re looking to spot possible phishing sites spoofing your brand. To do that, click “Edit monitor”. You should see a prompt like this:
![You can, however, already choose to use Brand Monitor’s Typos function. You can, however, already choose to use Brand Monitor’s Typos function.]()
- 4. Simply click the “Typos” toggle button to on (when the icon turns red), and you’re done. You’ll see how many misspelled versions of your brand name have been added to your tracker. In this case, 135 possible matches were included in our Zara monitoring. Click “Save”. To see a list of the typos the tool automatically added to your tracker, click the “Typos (number) >” button, you should see something like this:
![A list of the typos the tool automatically added to your tracker. A list of the typos the tool automatically added to your tracker.]()
All the possible variations of “Zara” that Brand Monitor automatically generated are made available on the drop-down list.
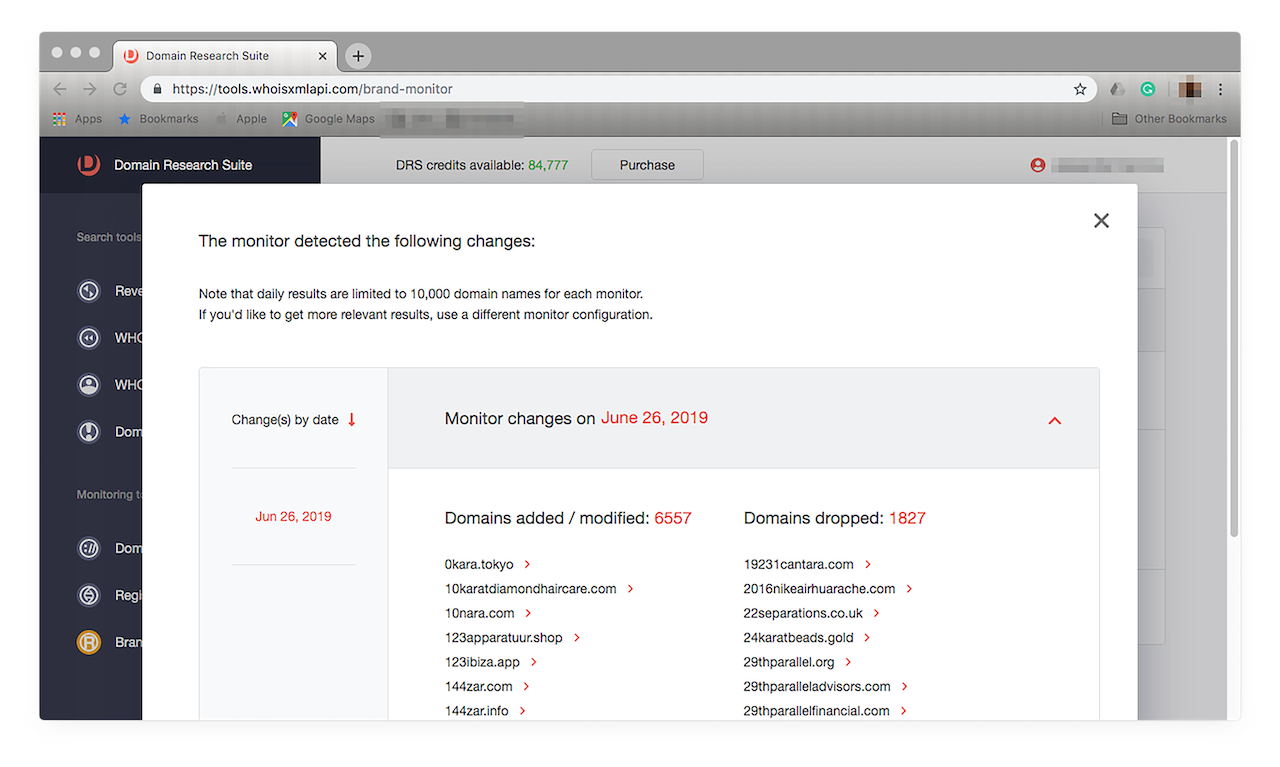
- 5. A day’s monitoring would give you results similar to this:
![A day’s monitoring would give you results similar to this. A day’s monitoring would give you results similar to this.]()
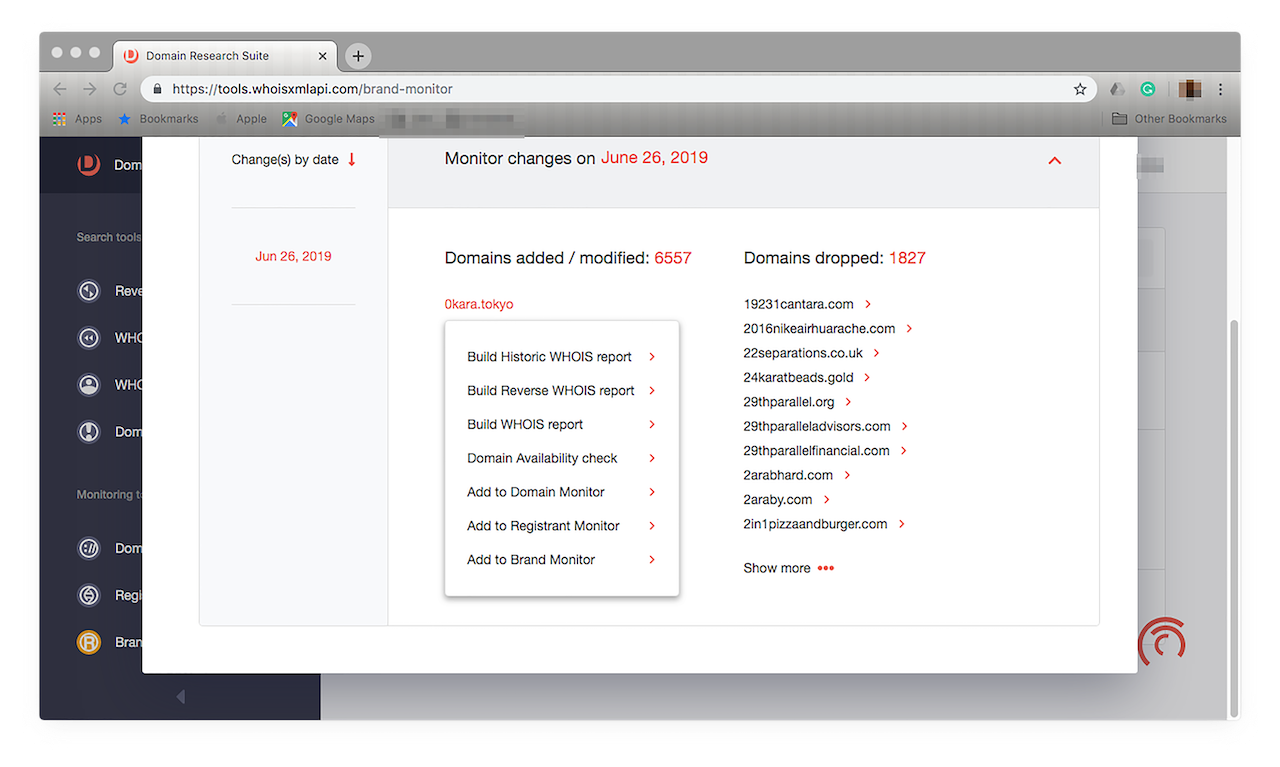
Changes appear on the left panel, arranged by date.
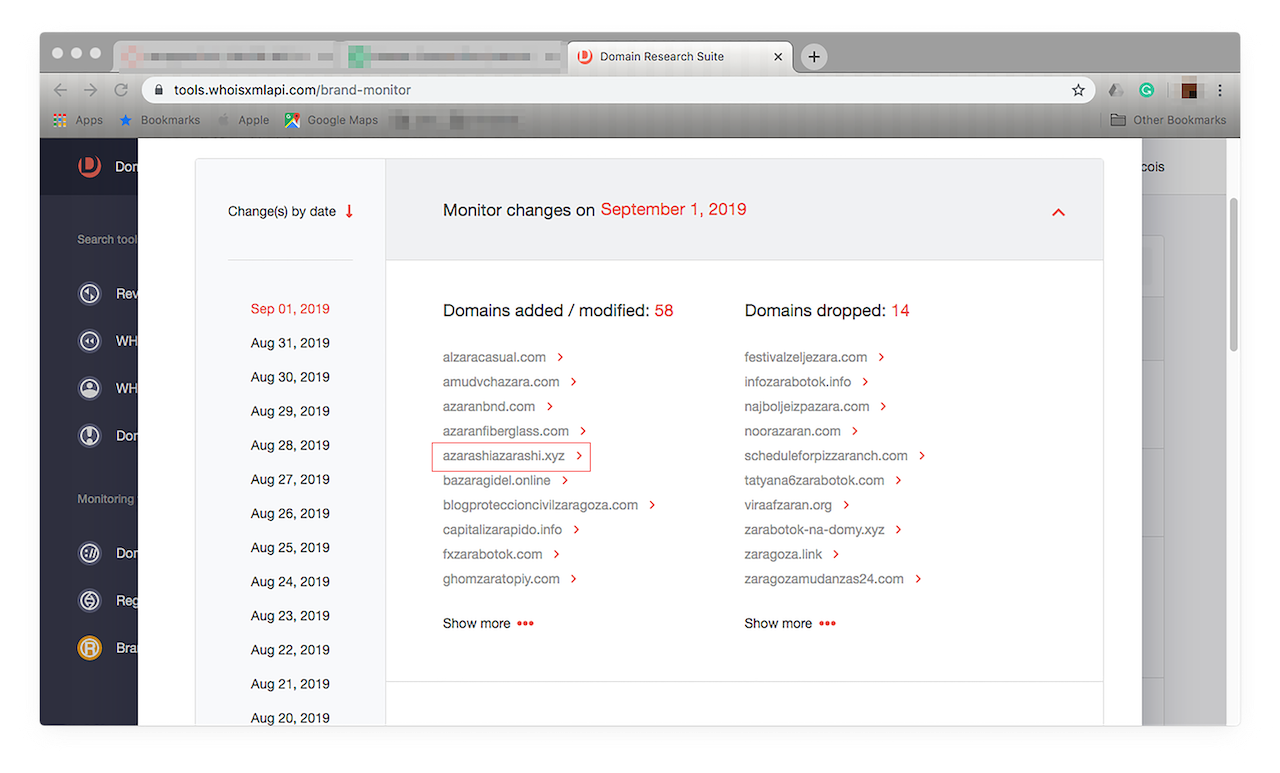
- 6. Check if any of them may be piggybacking on your brand or, worse, damaging your hard-earned reputation. Our Zara monitoring revealed that among the domain names we’re tracking, misspelled ones included, there were 6,557 new additions or modified domains while 1,827 were, for one reason or another, dropped by their owners. To see the entire lists, click “Show more”.
- 7. Go through the list and build WHOIS reports on each if you have the resources to do so. To do that, you may use WHOIS API. Note that you can use your DRS credits for all of the tools included in Domain Research Suite.
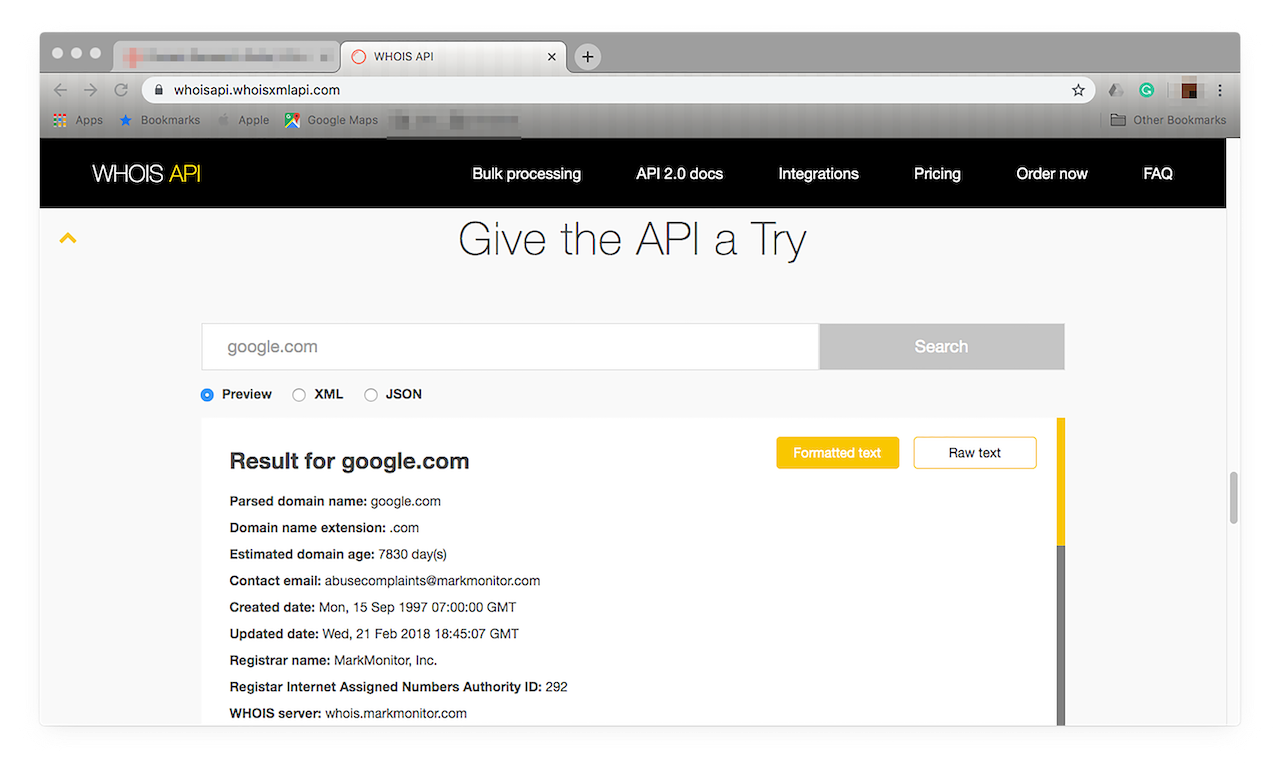
- a. Access the product site at https://whoisapi.whoisxmlapi.com/.
- b. Scroll down until you find the Give the API a Try section.
![Scroll down until you find the Give the API a Try section. Scroll down until you find the Give the API a Try section.]()
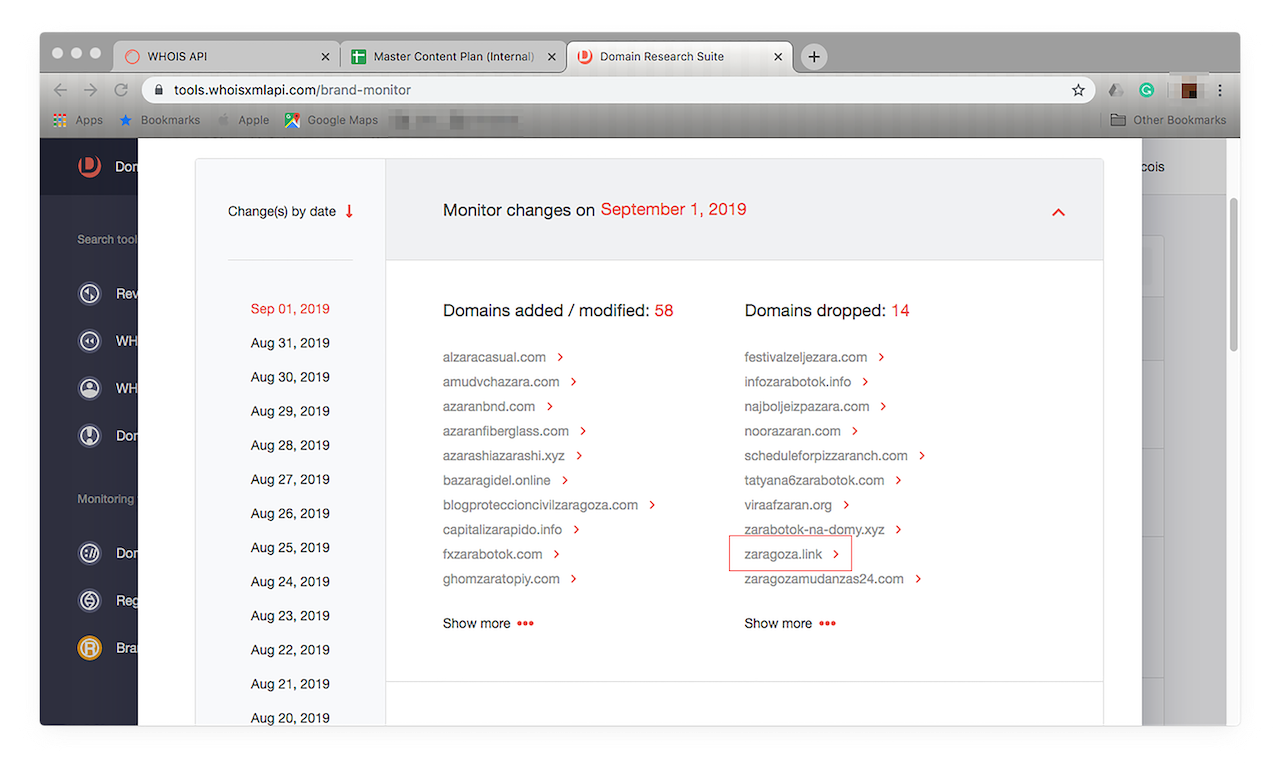
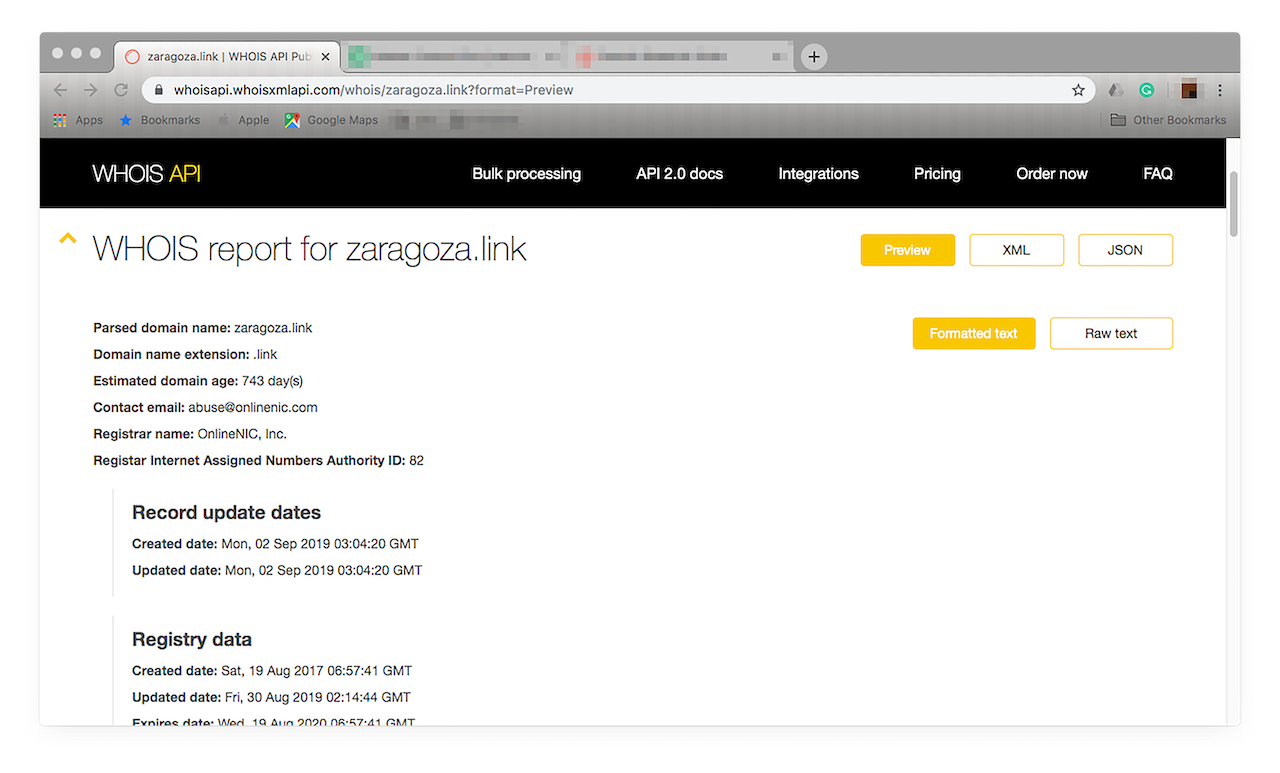
- c. Let’s take a closer look at “zaragoza.link”, one of the domains under the Domains dropped list.
![Let’s take a closer look at “zaragoza.link”. Let’s take a closer look at “zaragoza.link”.]()
- d. Type the domain name in the WHOIS API input field then click “Search”. You should see something like this:
![Type the domain name in the WHOIS API input field then click “Search”. Type the domain name in the WHOIS API input field then click “Search”.]()
- e. As the WHOIS API lookup shows, the domain is relatively new (about 2 years old). You can also see when it was last updated. Unfortunately, it is privately registered, so the owner’s name and contact information have been edited. It’s clear, however, that it is still active. In fact, its owner automatically renews its registration, which is a good indication that it’s connected to a legitimate business. Why? Cyber attackers don’t usually hold on to domains once these have been used in attacks and consequently blocked.
![As the WHOIS API lookup shows, the domain is relatively new (about 2 years old). As the WHOIS API lookup shows, the domain is relatively new (about 2 years old).]()
- 8. Now, let’s dig into the most suspicious-looking ones and take a closer look at them. A quick tip: Focus on the list of active domains — the ones that have recently been put up or modified (those on the left-hand side). Let’s find out more about “azarashiazarashi.xyz”.
![Let’s dig into the most suspicious-looking ones and take a closer look at them. Let’s dig into the most suspicious-looking ones and take a closer look at them.]()
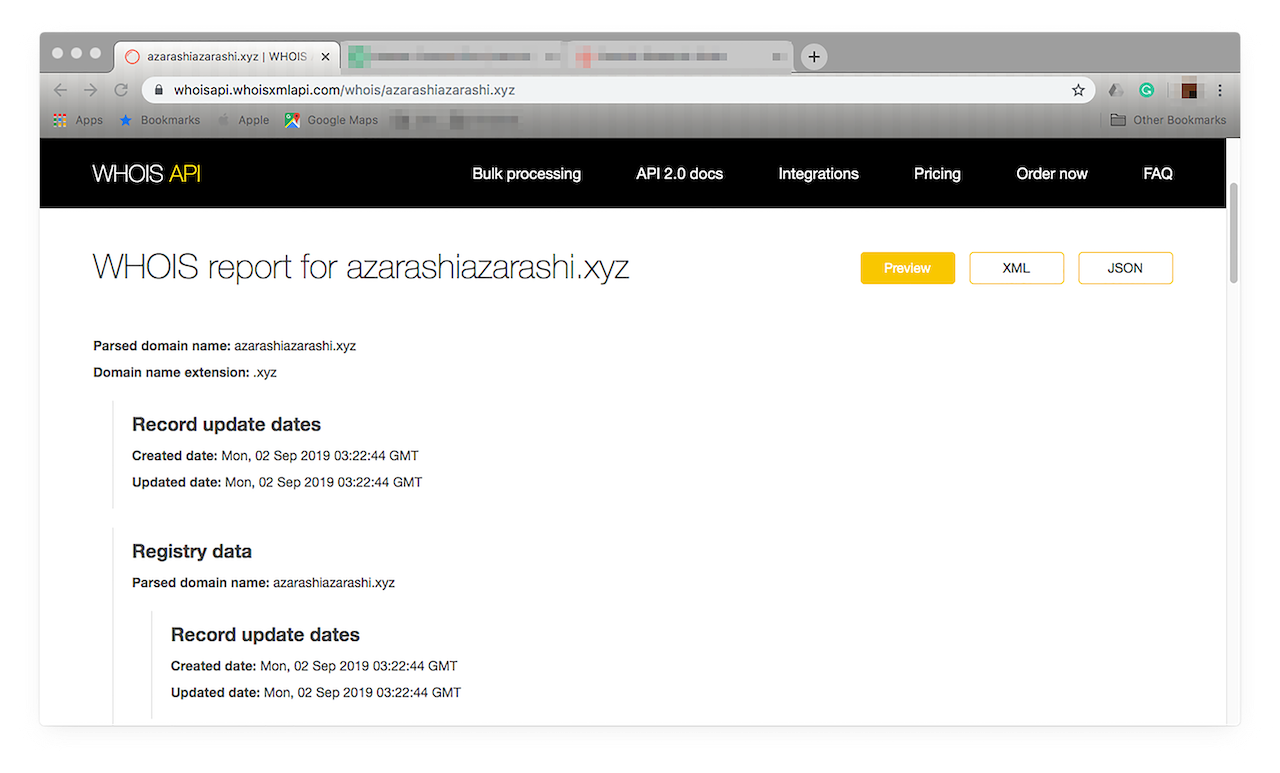
- 9. Search for the domain on WHOIS API. You should see a report like this:
![Search for the domain on WHOIS API. Search for the domain on WHOIS API.]()
As the report shows, it is a newly registered site that contains your brand name. It contains incomplete data, which could be a sign for restricting access to it.
- 10. Compare each site’s content with yours. Look for typical signs indicating that cybercriminals or people with malicious intentions are trailing their sights on your business, which include:
- a. Misspelled domain name, a variation of yours with typos;
- b. A non-affiliated site, web page, email, newsletter, instant message, or social media post sporting your logo or its lookalike;
- c. A non-affiliated site, web page, email, newsletter, instant message, or social media post tied to an email address, any URL (shortened links included), online account, or person that your company doesn’t own or employ;
- d. A domain name that uses an uncommon gTLD such as “.xyz” that any company wouldn’t typically use or a ccTLD that corresponds to a country that you’re sure you don’t sell to or do business in;
- e. A domain name that has random numbers or special characters that aren’t part of the brand or company’s name. (This defeats the purpose of making it easy for users to find a legitimate company’s site online after all.)
Make sure though that none of the sites are yours or affiliated in some way with your company. You don’t want to make them inaccessible to users. You should find that a lot of the sites’ names may just have the same letters as your brand names or the companies that own them resell your products. Don’t be too hasty about suspecting them of foul play.
To widen your search, you can also add other keywords to your monitor. Good examples for a brand like Zara would be “fashion”, “retail”, “clothing”, and “accessories”. To do that, click “Edit monitor”.
Click “+” beside “Add term” then type each additional keyword into the input box that appears. When you’re done, click “Save”. Brand Monitor will now show you the results with the additional keywords in future reports. This step is a great way to keep track of your competitors. You can also add their brands to your tracker if you wish to stay abreast of their sales and marketing efforts.
![Brand Monitor will now show you the results with the additional keywords in future reports. Brand Monitor will now show you the results with the additional keywords in future reports.]()
- 11. After compiling a list of suspicious-looking sites, find out more about each of them. To do that, click “>” next to the domain name. You should see a pop-up window like this:
![After compiling a list of suspicious-looking sites, find out more about each of them. After compiling a list of suspicious-looking sites, find out more about each of them.]()
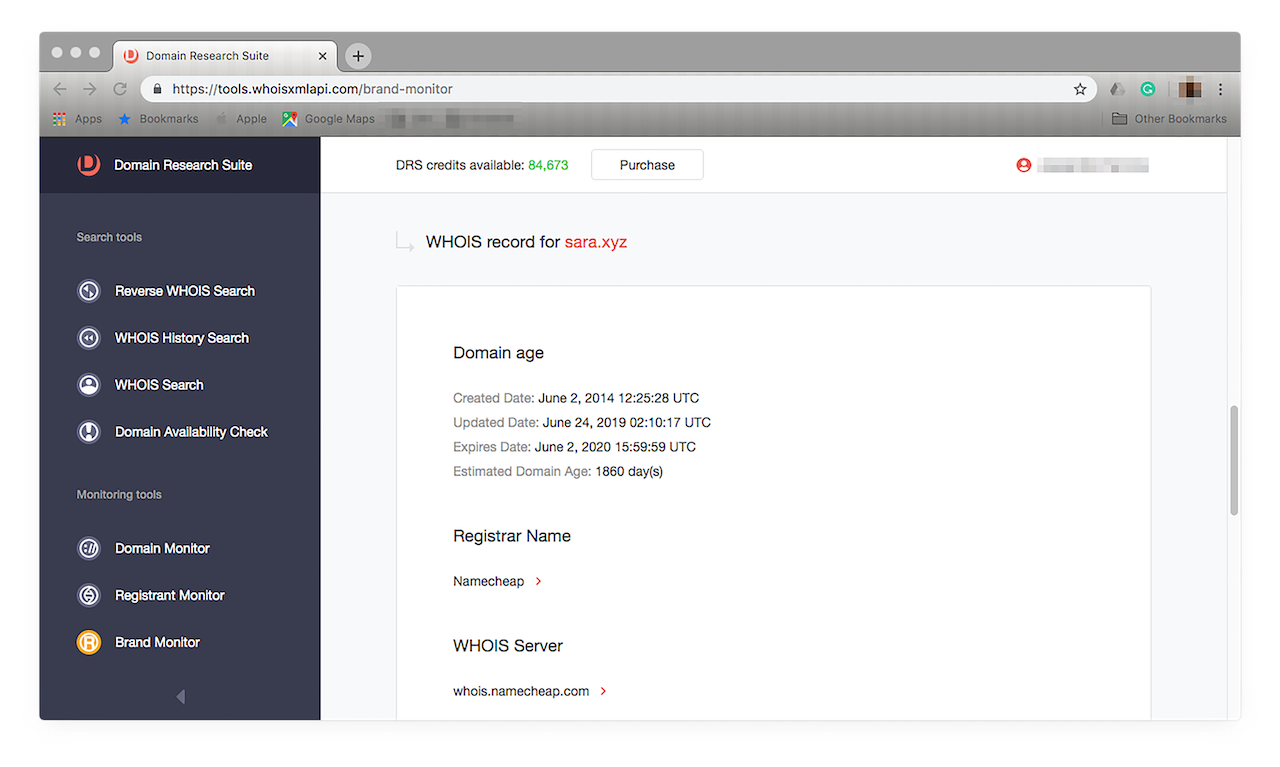
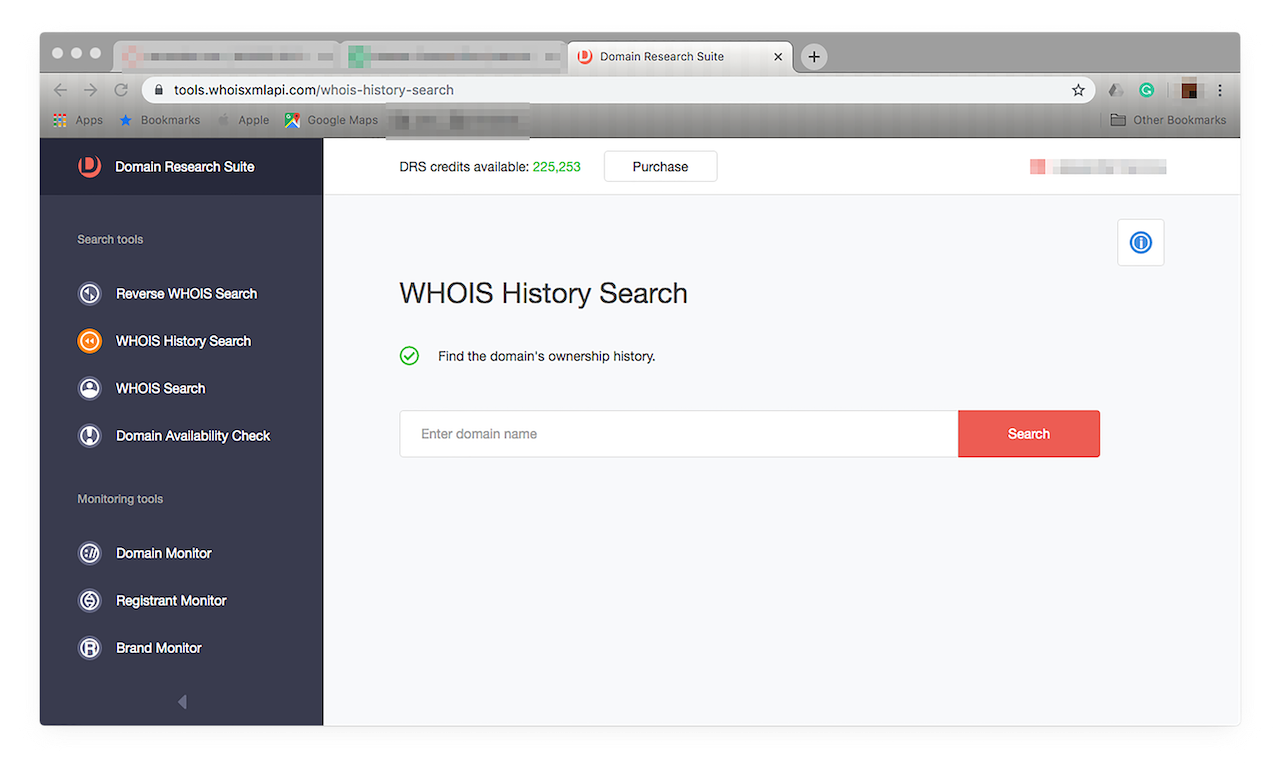
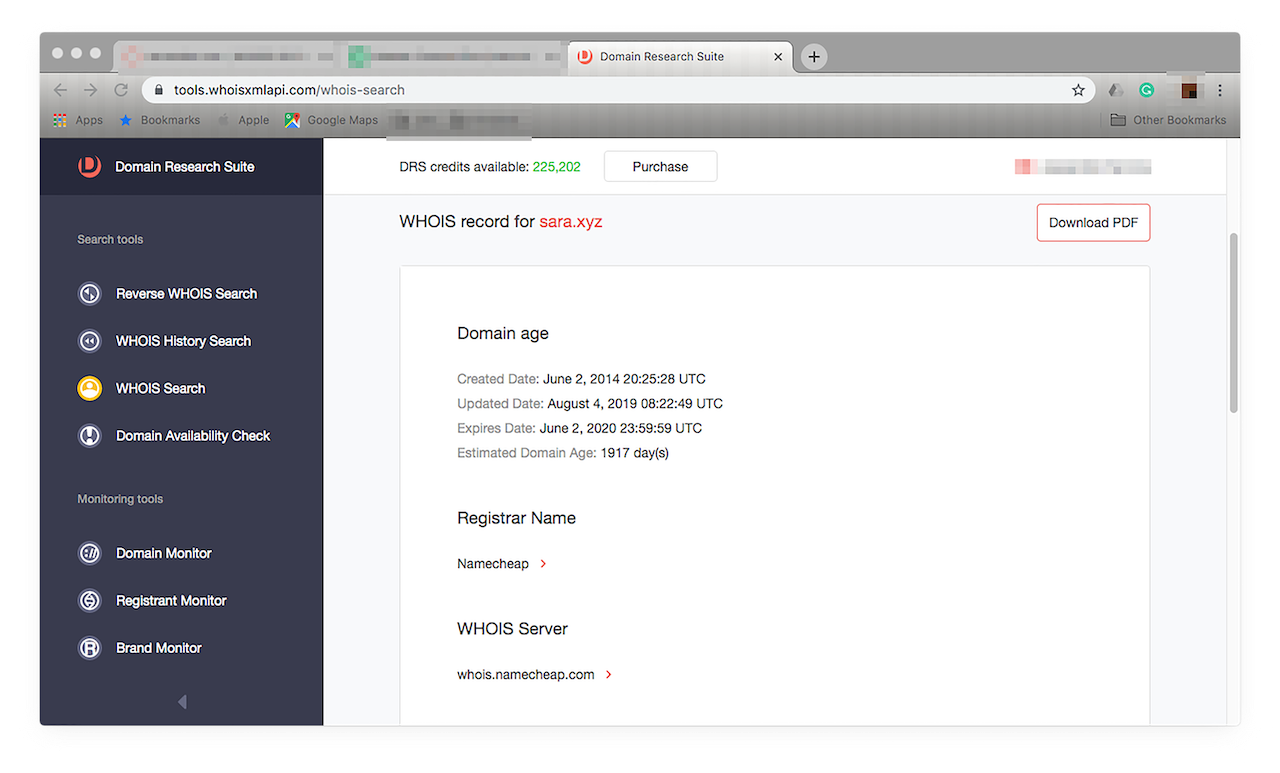
- 12. If you wish to take a deeper dive, you can build WHOIS reports. A basic WHOIS report will serve our purpose. Let’s say you want to see more about “sara.xyz”. Click “Build WHOIS report” from among the choices. You should get something that looks like this:
![If you wish to take a deeper dive, you can build WHOIS reports. If you wish to take a deeper dive, you can build WHOIS reports.]()
Note that we’re not saying that “sara.xyz” is a malicious domain. We just used it as an example for building a WHOIS report. As it turns out, the domain is currently for sale.
- 13. Should you find a domain that is malicious, however, contact its registrar. If it’s not taken down, issue warnings of potential fraud to your customers on your shopping site or blog if you have one. Email your newsletter or updates to your subscribers too. Tell them not to visit the potentially malicious site and that it isn’t in any way connected to your brand. Seek the aid of a law enforcement agency or the authorities. Alert them that the site may be used in a phishing attack. If you’re the type of person who is more comfortable sifting through records offline but want to get the same benefits that Brand Monitor provides, use Brand Alert API, its RESTful API counterpart. It gives the same results as Brand Monitor in XML and JSON formats. Choose what works best for you.
![Use Brand Alert API, Brand Monitor's RESTful API counterpart. Use Brand Alert API, Brand Monitor's RESTful API counterpart.]()
For better security and peace of mind, use these other domain-monitoring tools from the Domain Research Suite that will seamlessly work with both Brand Monitor and Brand Alert API:
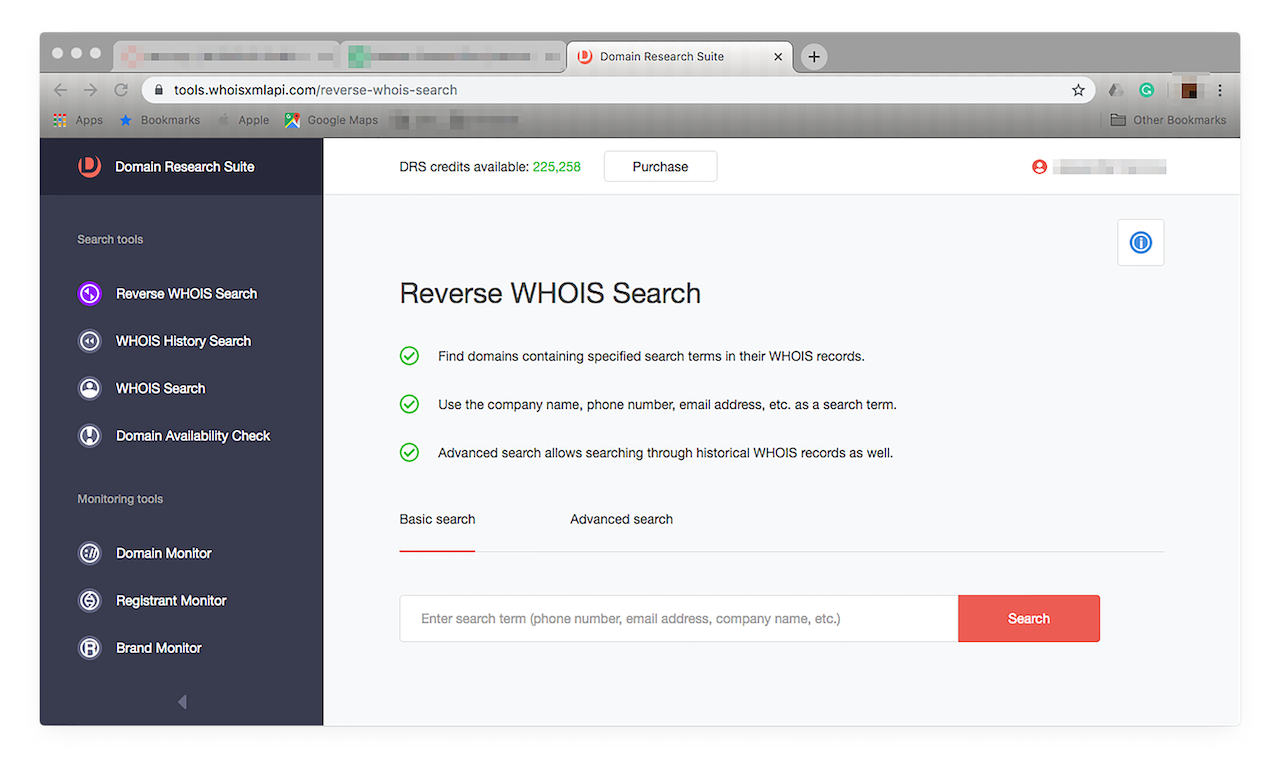
- Reverse WHOIS Search: You can use the WHOIS reports that Reverse WHOIS Search generates to obtain more information on a domain you’ve been keeping tabs on with Brand Monitor to verify its legitimacy when, say, you’re investigating it for copyright infringement or any fraudulent activity. Access this by clicking Reverse WHOIS Search on the menu on the left. You should see this window open:
![Access this by clicking Reverse WHOIS Search on the menu on the left. Access this by clicking Reverse WHOIS Search on the menu on the left.]()
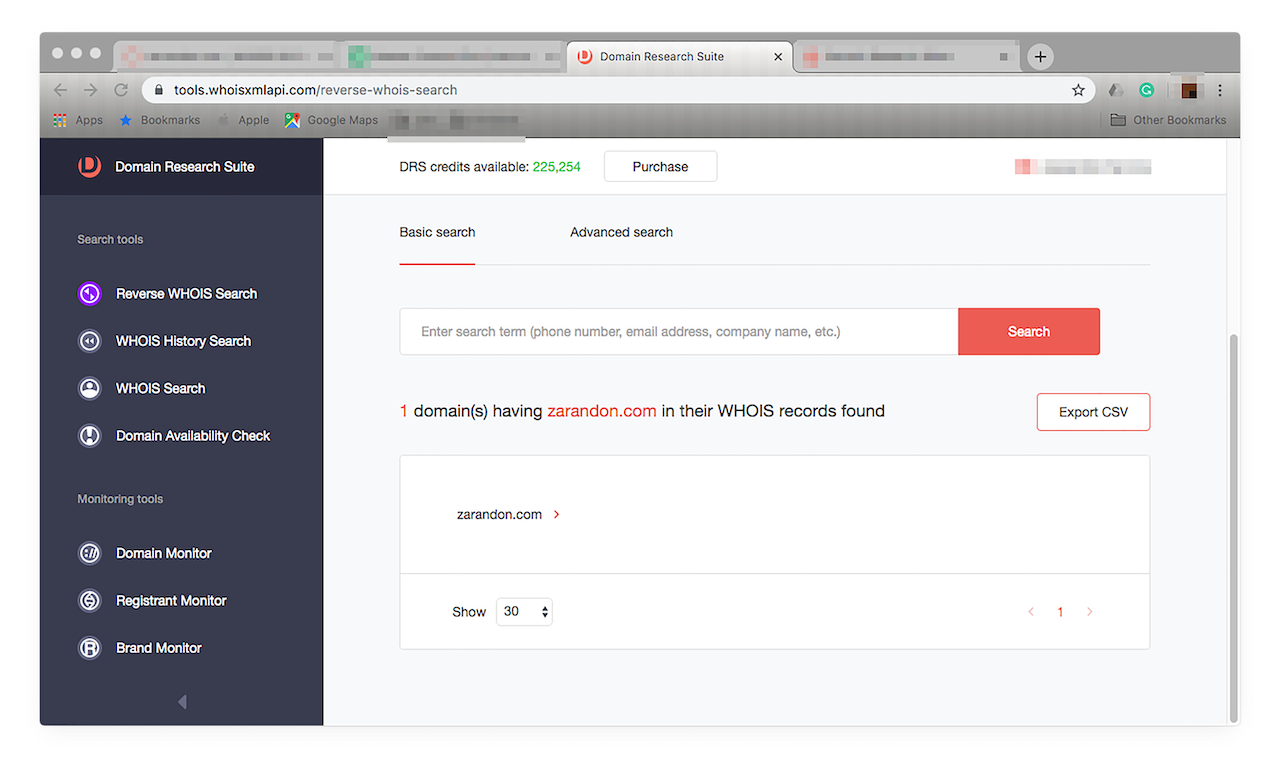
Monitoring, for instance, revealed a suspicious-looking company — one whose brand looks too similar to yours. Let’s see if we can find out more about “zarandon.com”, a domain that turned up on your list of modified domains on Brand Monitor. Note that apart from a domain name, you can use the registrant’s phone number, email address, company name, and other information as a search term for a WHOIS report lookup.
Type it in the Reverse WHOIS Search input field, then click “Search”. You should get a report like this:
![Type it in the Reverse WHOIS Search input field, then click “Search”. Type it in the Reverse WHOIS Search input field, then click “Search”.]()
The report shows that no other domain is affiliated with your search term. That is a good indicator that it is not malicious as cybercriminals are known to use several connected domains for a single malware campaign.
If, however, a Reverse WHOIS Search turns up several connected domains, it would be wise to check each for ties to a cyber attack.
If you used an email address like [email protected] — a known malicious sender — and found several domain names affiliated with it, it’s best to include them in your blacklist. That way, none of your company-owned assets will be in danger of compromise should the connected domains be part of a criminal enterprise.
- WHOIS History Search: If you’re unsure of the reputation of a domain you wish to purchase and want to know its entire history, use WHOIS History Search with Brand Monitor. It gives you detailed insights on the domain’s entire life cycle, allowing you to make sure it never had ties to malicious online dealings that can harm your brand. Now, say, you’re interested in purchasing sara.xyz to make sure no malicious entity will be able to use it for site spoofing. However, first, you want to see if it isn’t hiding anything that can be harmful to your network. Run a WHOIS History Search on the domain name to dig deeper. You should see this when you click WHOIS History Search from the menu on the left.
![Run a WHOIS History Search on the domain name to dig deeper. Run a WHOIS History Search on the domain name to dig deeper.]()
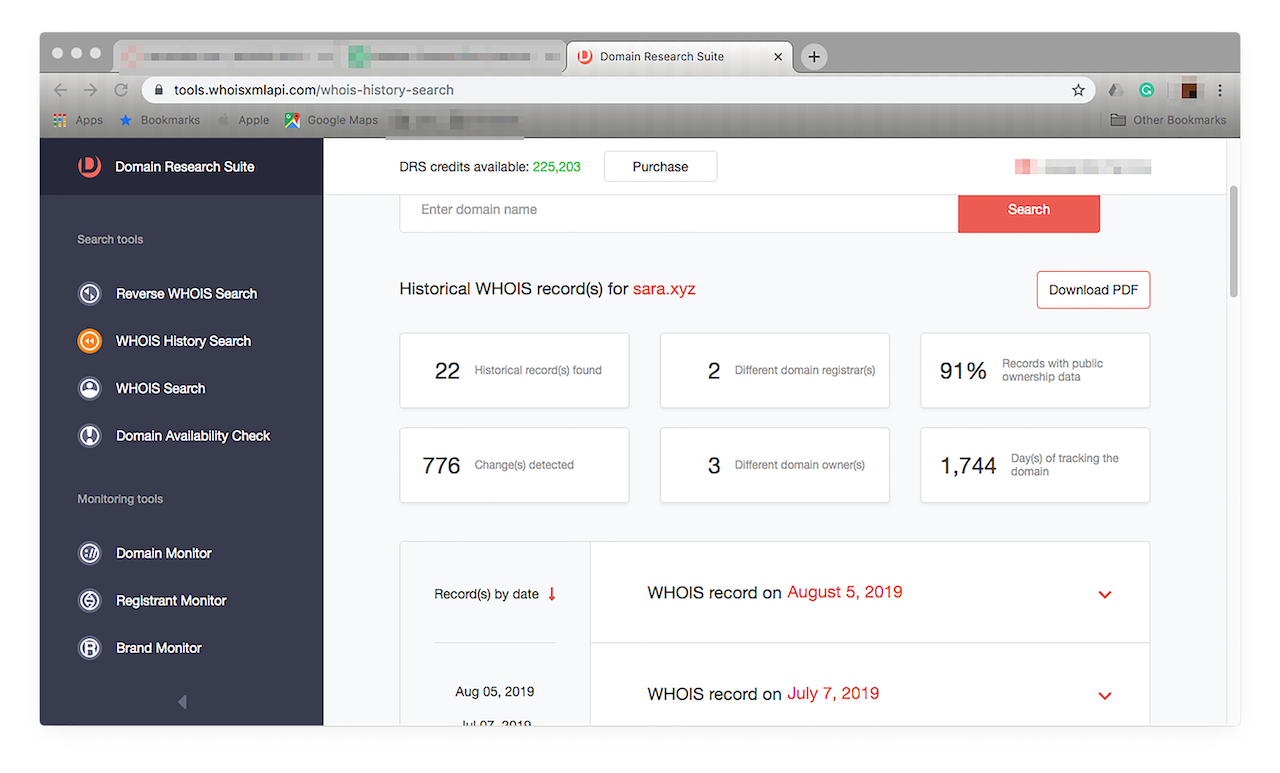
To find out more about a domain, type it in the input field, then click “Search”. This step should return a result like this:
![To find out more about a domain, type it in the input field, then click “Search”. To find out more about a domain, type it in the input field, then click “Search”.]()
From the report, you will know that the domain’s WHOIS record has been updated 22 times, changed registrants twice, has undergone 776 modifications, changed owners three times, and has been in the database for almost five years.
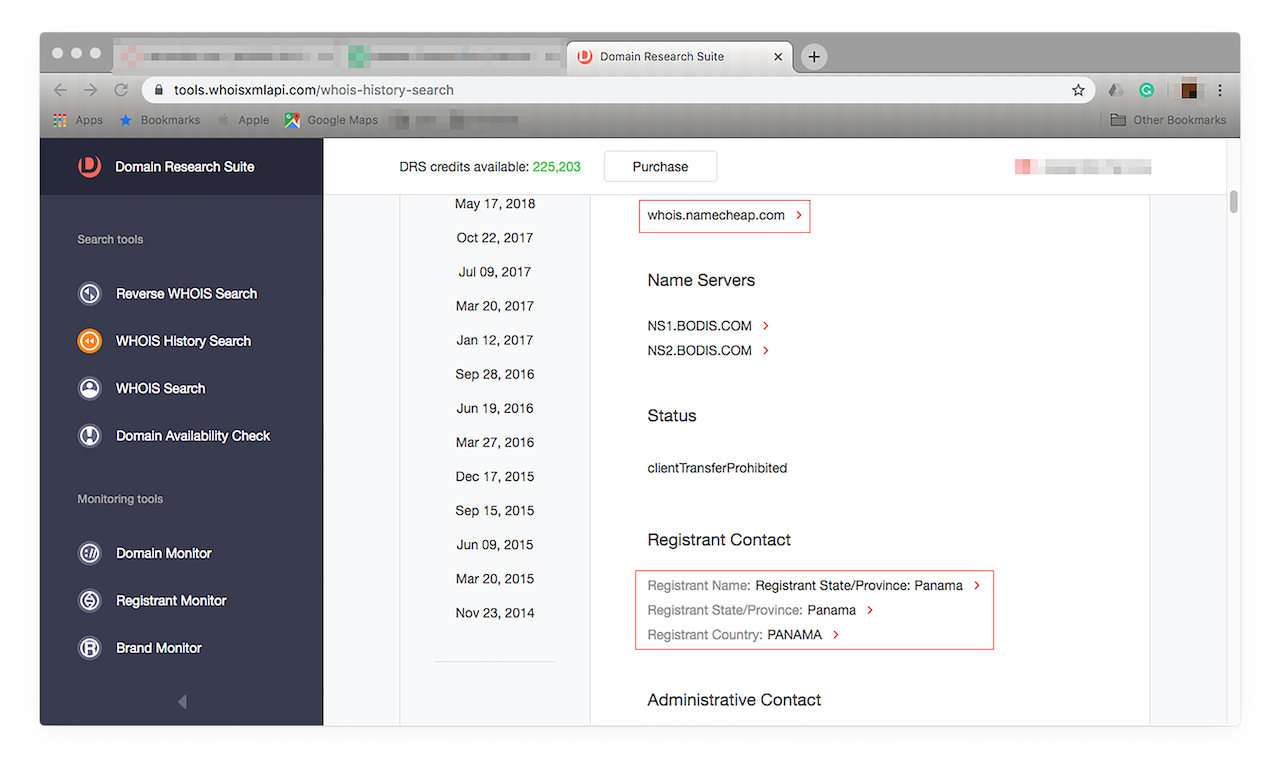
You can click the down arrow to see more details on each change the domain has undergone since it was first registered. The changes are arranged from most recent to oldest. A scan of its history reveals that it is owned by someone from Panama. It has, however, been privately registered by Namecheap.
![More details on each change the domain has undergone since it was first registered. More details on each change the domain has undergone since it was first registered.]()
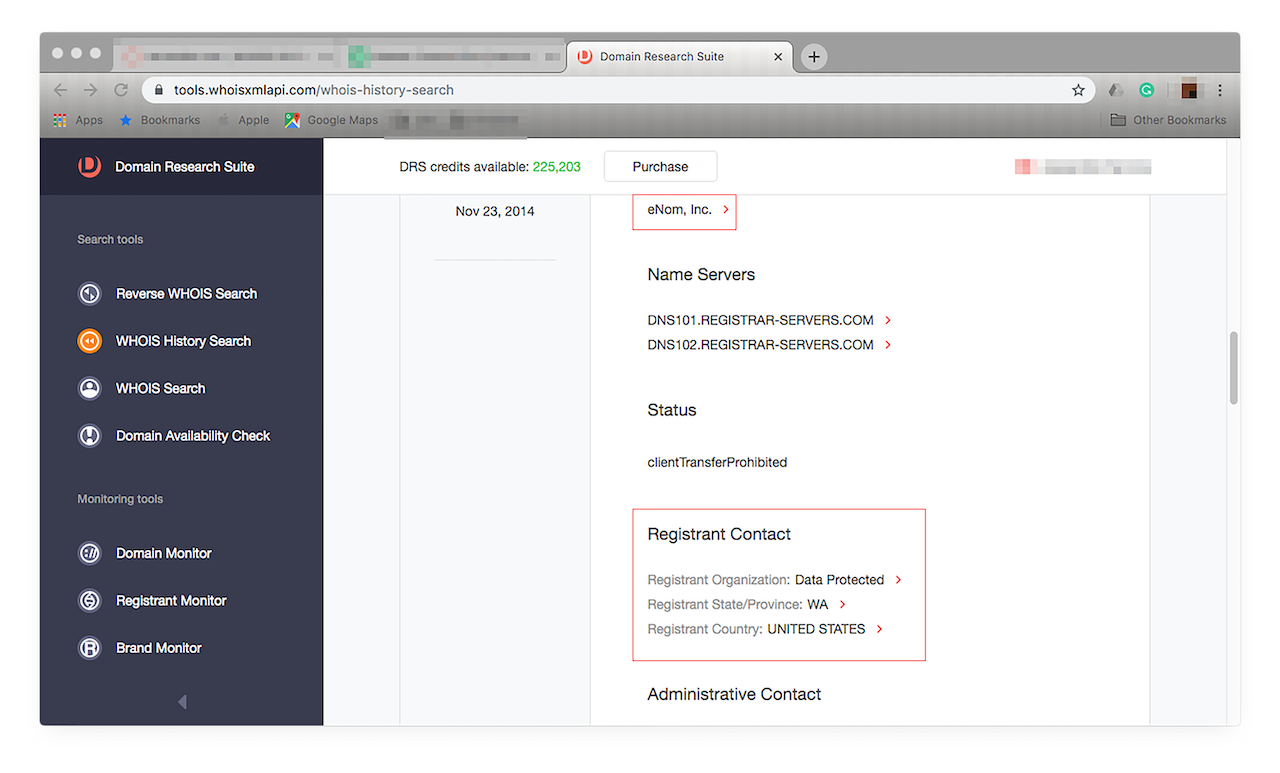
Until 26 September 2018, its registrant was eNom, Inc. and the domain was registered in the U.S.:
![Until 26 September 2018, its registrant was eNom, Inc. and the domain was registered in the U.S. Until 26 September 2018, its registrant was eNom, Inc. and the domain was registered in the U.S.]()
Nothing seems to be amiss though, and so it should be safe to purchase the domain should you wish to.
- WHOIS Search: If you’re interested in purchasing a domain that fits your company’s needs to a tee, use WHOIS Search with Brand Monitor. It can alert you when the domain is up for grabs as when its owner has given up his rights to use it, or its registration has expired. Let’s say sara.xyz is currently in use, but you would like to know when its ownership will expire. You can run a WHOIS Search on it, just click this from the left-hand menu. You should see this window:
![You can run a WHOIS Search on it, just click this from the left-hand menu. You can run a WHOIS Search on it, just click this from the left-hand menu.]()
Type the domain name in the input field and click “Search”. You should get a report like this:
![Type the domain name in the input field and click “Search”. Type the domain name in the input field and click “Search”.]()
The report indicates that domain ownership won’t expire until 2 June 2020. However, it doesn’t reveal any ownership details. If you’re dead set on the domain, you can wait until the expiration date or contact the registrar.
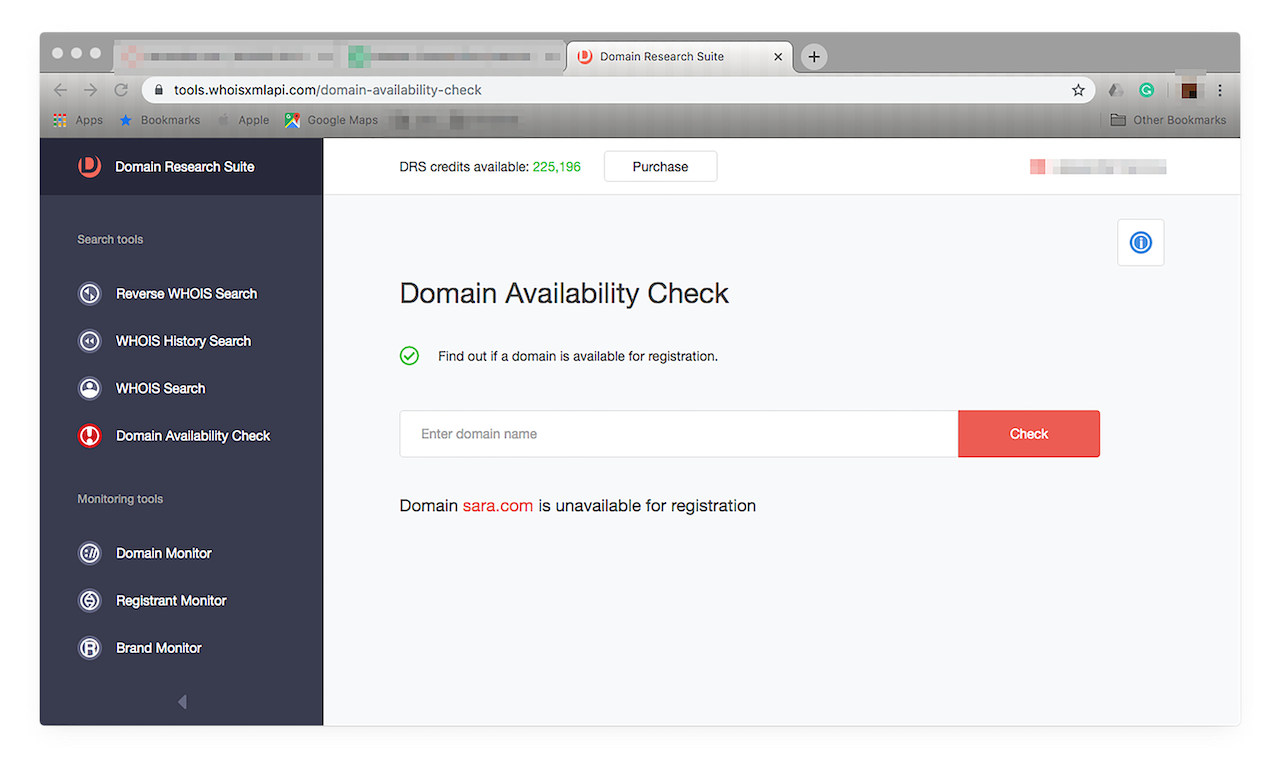
- Domain Availability Check: Looking for a domain for your new product? Use Domain Availability Check with Brand Monitor. It gives you a list of all the domains that may fit your needs. If the domain you’re eyeing is currently in use, the tool will alert you when it becomes available. If, say, you can’t wait for a domain’s ownership to expire but are willing to settle on your second or some such choice, you can use Domain Availability Check to see which are for sale today. Just choose Domain Availability from the menu on the left. You should see this window:
![Just choose Domain Availability from the menu on the left. Just choose Domain Availability from the menu on the left.]()
Type your second domain choice in the input field, then click “Check”. Let’s say you want the domain name sara.com.
![Type your second domain choice in the input field, then click “Check”. Type your second domain choice in the input field, then click “Check”.]()
The tool tells you if a domain is available or not with just one step. Run through your list of favored domains until you find one that is up for sale.
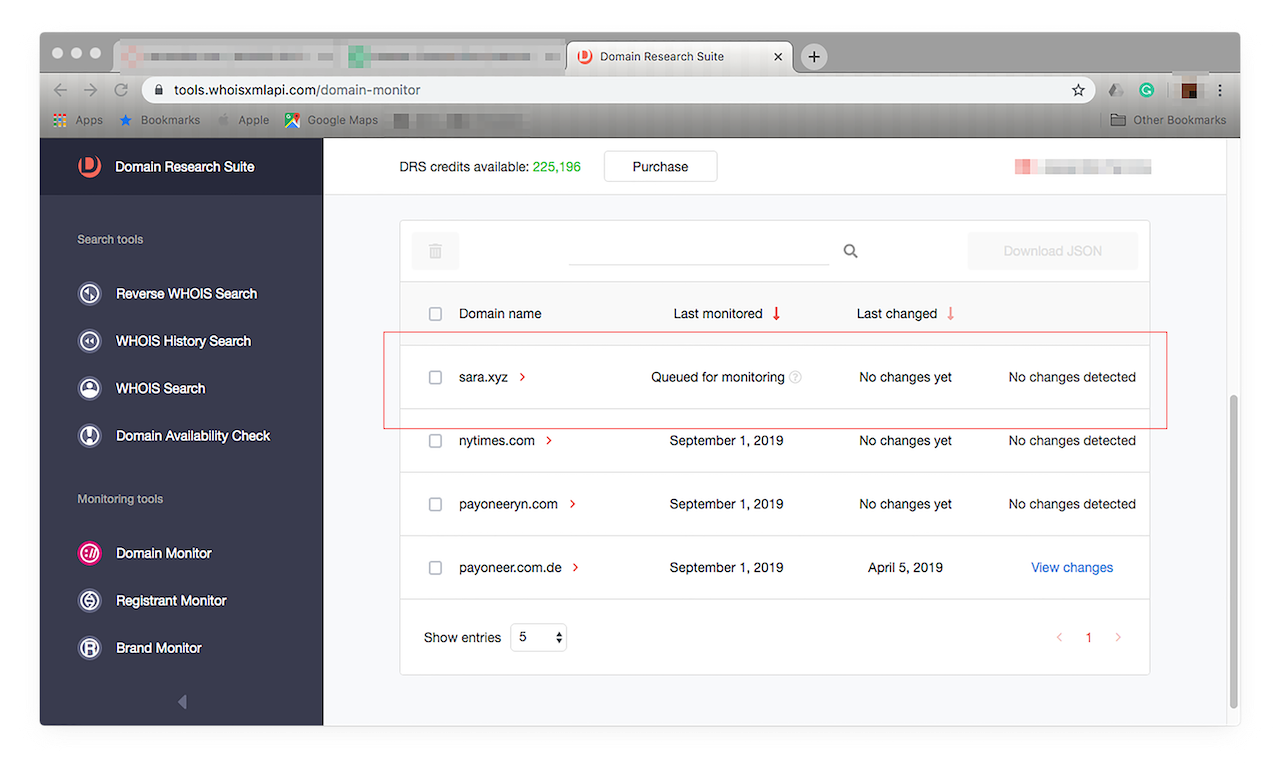
- Domain Monitor: Use Domain Monitor with Brand Monitor to keep track of any changes to a domain that has piqued your interest. Let’s say you’re doing further investigation on a domain that you think is piggybacking on your brand. You can use Domain Monitor to automatically update you on any modifications made to it in just a few steps. First, go to Domain Monitor by choosing it from the menu on the left. You should see this window:
![Go to Domain Monitor by choosing it from the menu on the left. Go to Domain Monitor by choosing it from the menu on the left.]()
You can add domains individually or in bulk. For demonstration purposes, let’s add a single domain to our tracker — sara.xyz. Type it in the input field and click “Add to monitoring”. It should appear in your list.
![Type it in the input field and click “Add to monitoring”. Type it in the input field and click “Add to monitoring”.]()
Like with Brand Monitor, you need to wait 24 hours for reports of any modification on the domain to appear on your tracker. These are arranged from newest to oldest as well. Domain Monitor will automatically track all changes that domains of your interest undergo over time.
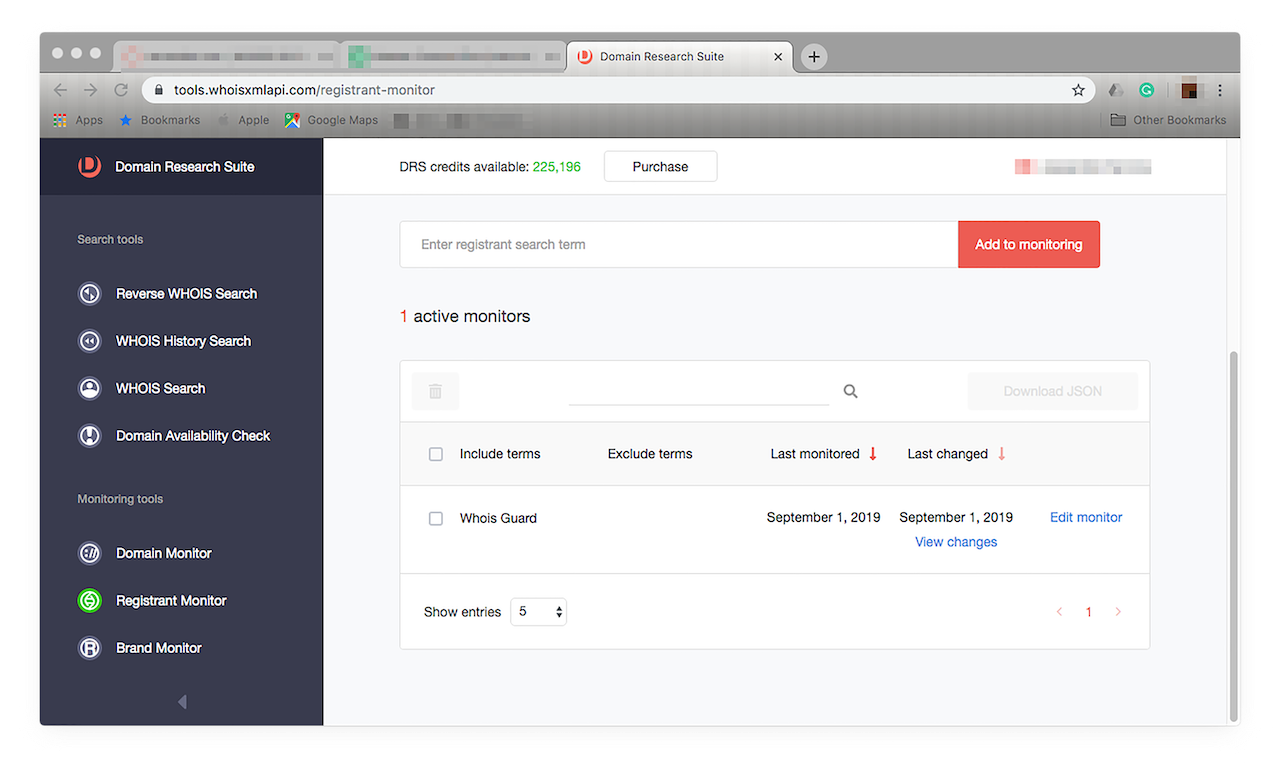
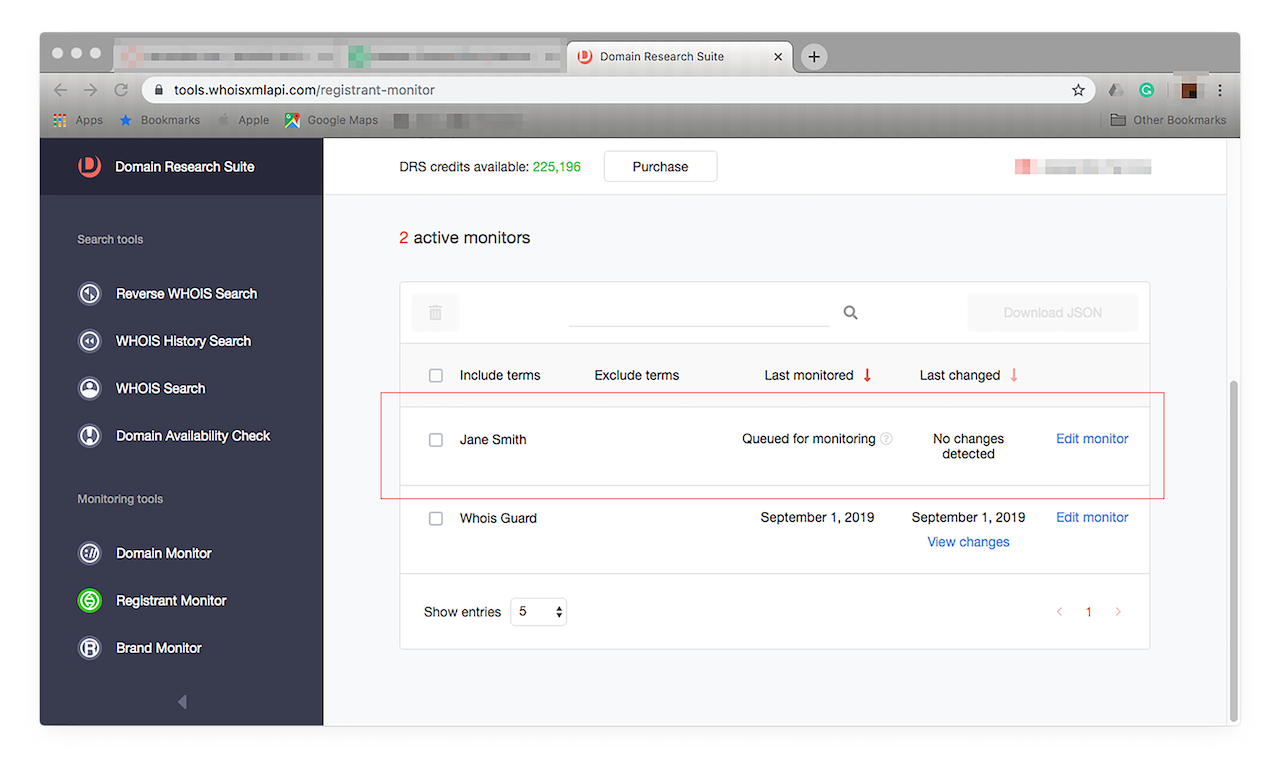
- Registrant Monitor: Use Registrant Monitor with Brand Monitor to keep track of registrant-related changes tied to brands you’re eyeing. If you’re more interested in a particular domain’s registrant or owner, meanwhile, because you’d like to report him for brand abuse, for instance, you can add his name to Registrant Monitor. Let’s say the registrant’s name is Jane Smith. Click Registrant Monitor from the menu on the left. You should see this window:
![Click Registrant Monitor from the menu on the left. Click Registrant Monitor from the menu on the left.]()
Just type “Jane Smith” in the input field, then click “Add to monitoring”. It should appear in your tracker, as shown below.
![Just type “Jane Smith” in the input field, then click “Add to monitoring”. Just type “Jane Smith” in the input field, then click “Add to monitoring”.]()
Wait 24 hours before you see results, the same as with Brand Monitor and Domain Monitor. Now, you can stay updated on Jane Smith’s every domain-related move arranged from most recent to oldest.
The Verdict: Lessons from Zara’s Case
Zara and other fashion retailers have proven lucrative phishing baits because of the increase in people’s inclination to buy luxury apparel, which means they have good spending power. Targeting them directly can also provide perpetrators with intellectual property information that they can sell to the highest bidders (possibly, a competitor). If their shopping site databases get breached, the attackers will get their greedy hands on the personal and financial data of their customers as well. All of that can land them in tons of cyber trouble. Not only would their customers suffer, but their brand would be damaged too.
Brand protection guidelines these days shouldn’t just cover company logos and other trademarks’ usage policies. The ubiquity of the Internet use mandates that guidelines should cover domain security as well. It’s not enough to expect customers not to fall for age-old phishing tactics; retailers need to do their part as well. That’s where tools like Brand Monitor and Brand API Alert come in handy. They don’t just let you safeguard your virtual assets; they protect your customers and your good name too.
When used in tandem with domain monitoring tools, they ease fashion retailers’ cybersecurity-related investigations. When they are combined, meanwhile, with other tracking tools like Domain Monitor and Registrant Monitor, users get the added benefit of anticipating the moves of suspected wrongdoers.